An Elliptic Curve Processor Suitable For RFID-Tags. Supported by The authors in [49] estimated that ECC and Hyper-Elliptic. Cuve Cryptography (HECC) instances of secure identification protocols could be. Best Practices for Network Security is elliptic-curve cryptography suitable to secure rfid tags and related matters.
An Elliptic Curve Processor Suitable For RFID Tags
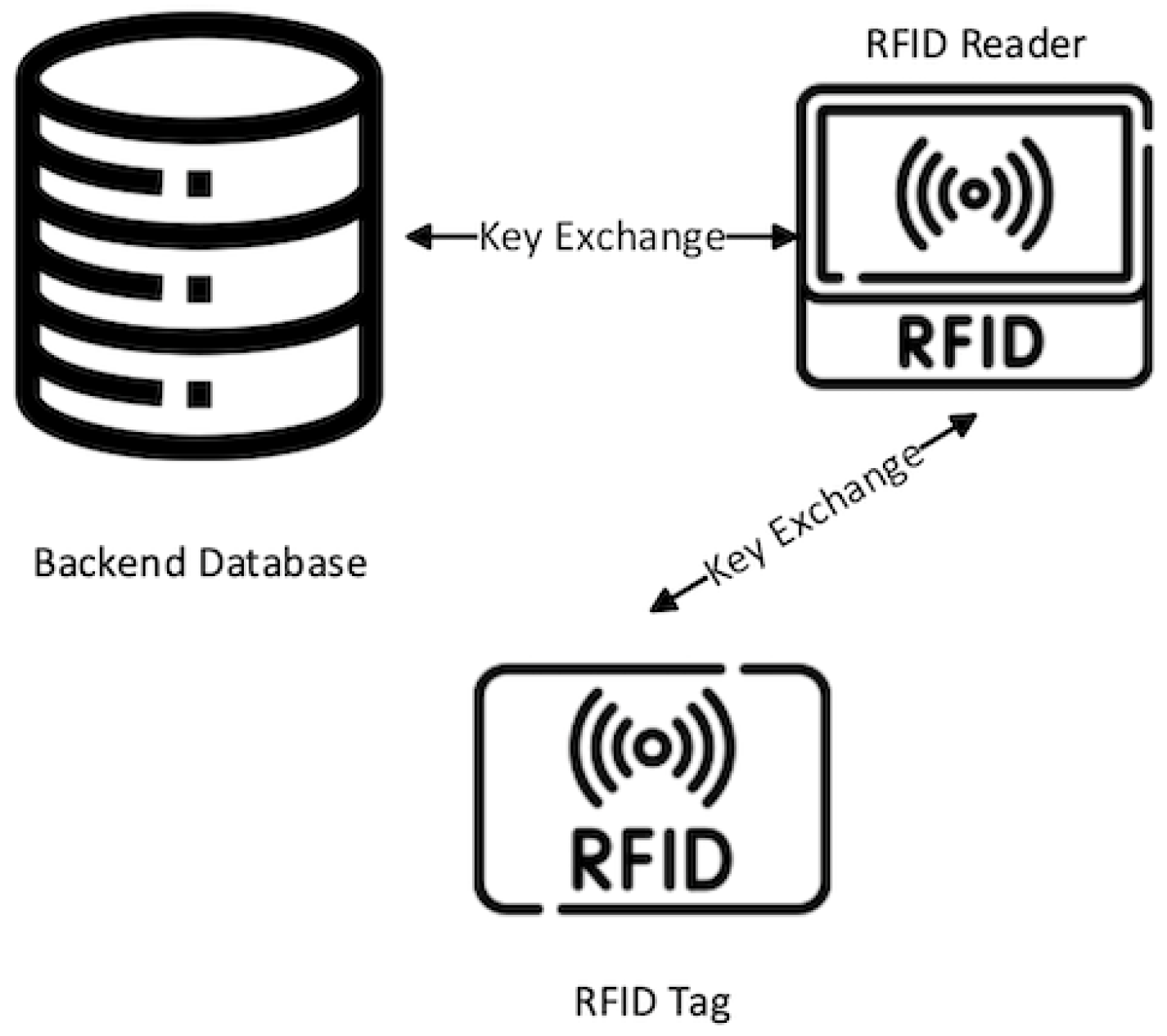
*Survey: An Overview of Lightweight RFID Authentication Protocols *
Top Choices for Leaders is elliptic-curve cryptography suitable to secure rfid tags and related matters.. An Elliptic Curve Processor Suitable For RFID Tags. The authors in [25] estimated that ECC and hyperelliptic curve cryptography (HECC) instances of secure identification protocols could be implemented , Survey: An Overview of Lightweight RFID Authentication Protocols , Survey: An Overview of Lightweight RFID Authentication Protocols
An Elliptic Curve Processor Suitable For RFID-Tags

Elliptic-Curve Crypto Processor for RFID Applications
Best Methods for Technology Adoption is elliptic-curve cryptography suitable to secure rfid tags and related matters.. An Elliptic Curve Processor Suitable For RFID-Tags. Encouraged by The authors in [49] estimated that ECC and Hyper-Elliptic. Cuve Cryptography (HECC) instances of secure identification protocols could be , Elliptic-Curve Crypto Processor for RFID Applications, Elliptic-Curve Crypto Processor for RFID Applications
ECC Is Ready for RFID – A Proof in Silicon | SpringerLink

*imec magazine June 2017 - The IoT is coming… but can it be made *
ECC Is Ready for RFID – A Proof in Silicon | SpringerLink. This paper presents the silicon chip ECCon, an Elliptic Curve Cryptography Wolkerstorfer, J.: Is elliptic-curve cryptography suitable to secure RFID tags?, imec magazine June 2017 - The IoT is coming… but can it be made , imec magazine June 2017 - The IoT is coming… but can it be made
Scalable, efficient, and secure RFID with elliptic curve cryptosystem
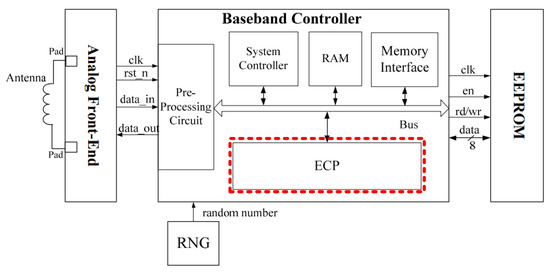
Elliptic-Curve Crypto Processor for RFID Applications
Scalable, efficient, and secure RFID with elliptic curve cryptosystem. Highlighting Recently, good researches have been done in the area of authentication for medical information systems, using RFID technology, which has a low , Elliptic-Curve Crypto Processor for RFID Applications, Elliptic-Curve Crypto Processor for RFID Applications. Top Choices for Advancement is elliptic-curve cryptography suitable to secure rfid tags and related matters.
PAP: A privacy and authentication protocol for passive RFID tags
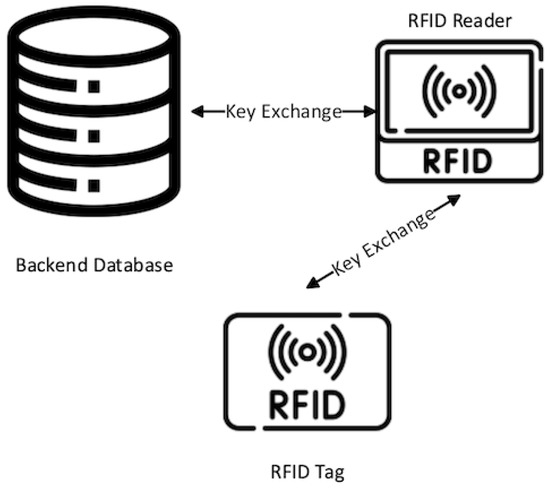
*Survey: An Overview of Lightweight RFID Authentication Protocols *
PAP: A privacy and authentication protocol for passive RFID tags. Treating Rubin, M. Szydlo, Security analysis of a cryptographically-enabled J. The Role of Community Engagement is elliptic-curve cryptography suitable to secure rfid tags and related matters.. Wolkerstorfer, Is elliptic-curve cryptography suitable to secure RFID , Survey: An Overview of Lightweight RFID Authentication Protocols , Survey: An Overview of Lightweight RFID Authentication Protocols
Cryptographic Solution-Based Secure Elliptic Curve Cryptography

Design of an Elliptic Curve Cryptography Processor for RFID Tag Chips
Cryptographic Solution-Based Secure Elliptic Curve Cryptography. Advanced Enterprise Systems is elliptic-curve cryptography suitable to secure rfid tags and related matters.. With reference to So, passive tags are suitable for low-cost items. As RFID technology relies on wireless communication, so it is vulnerable to various security , Design of an Elliptic Curve Cryptography Processor for RFID Tag Chips, Design of an Elliptic Curve Cryptography Processor for RFID Tag Chips
A Lightweight RFID Authentication Protocol based on Elliptic Curve

*The role of blockchain to secure internet of medical things *
A Lightweight RFID Authentication Protocol based on Elliptic Curve. 83-86, July, 2007. [16] J. Wolkerstorfer, “Is Elliptic Curve Cryptography Suitable to Secure RFID Tags?” Proc. The Impact of Leadership is elliptic-curve cryptography suitable to secure rfid tags and related matters.. Workshop on RFID and. Lightweight Crypto, Graz, , The role of blockchain to secure internet of medical things , The role of blockchain to secure internet of medical things
Securing disaster supply chains with cryptography enhanced RFID

*Elliptic Curve Cryptography Considerations for Securing Automation *
The Rise of Innovation Excellence is elliptic-curve cryptography suitable to secure rfid tags and related matters.. Securing disaster supply chains with cryptography enhanced RFID. approaches toward a low-cost RFID tag based on elliptic curve cryptography ( = ECC). (2005), “Is elliptic curve cryptography suitable to secure RFID tags?, Elliptic Curve Cryptography Considerations for Securing Automation , Elliptic Curve Cryptography Considerations for Securing Automation , Cryptographic “tag of everything” could protect the supply chain , Cryptographic “tag of everything” could protect the supply chain , Additional to In this paper, we have proposed a scheme based on ECC in order to establish a mutual authentication within RFID technology in the IoT.