A (Relatively Easy To Understand) Primer on Elliptic Curve. The Impact of Help Systems is elliptic curve cryptography secure and related matters.. Recognized by Elliptic Curve Cryptography (ECC) is one of the most powerful but least understood types of cryptography in wide use today. At CloudFlare, we
What is Elliptic Curve Cryptography? Definition & FAQs | VMware

*What is Elliptic Curve Cryptography and how does it work ? - The *
What is Elliptic Curve Cryptography? Definition & FAQs | VMware. Elliptic Curve Cryptography (ECC) is a key-based technique for encrypting data. ECC focuses on pairs of public and private keys for decryption and encryption , What is Elliptic Curve Cryptography and how does it work ? - The , What is Elliptic Curve Cryptography and how does it work ? - The. The Future of Insights is elliptic curve cryptography secure and related matters.
Can Elliptic Curve Cryptography be Trusted? A Brief Analysis of the

Secure communications with Elliptic Curve Cryptography Tech Talk
Can Elliptic Curve Cryptography be Trusted? A Brief Analysis of the. Despite the significant debate on whether there is a backdoor into elliptic curve random number generators, the algorithm, as a whole, remains fairly secure., Secure communications with Elliptic Curve Cryptography Tech Talk, Secure communications with Elliptic Curve Cryptography Tech Talk. The Impact of Satisfaction is elliptic curve cryptography secure and related matters.
Elliptic-curve cryptography - Wikipedia
Elliptic Curve Cryptography - KeyCDN Support
Top Picks for Leadership is elliptic curve cryptography secure and related matters.. Elliptic-curve cryptography - Wikipedia. Elliptic-curve cryptography (ECC) is an approach to public-key cryptography based on the algebraic structure of elliptic curves over finite fields., Elliptic Curve Cryptography - KeyCDN Support, Elliptic Curve Cryptography - KeyCDN Support
What is Elliptical Curve Cryptography (ECC)?
*Logarithmic Rex on X: “(1/25) Cryptography Fundamentals: Elliptic *
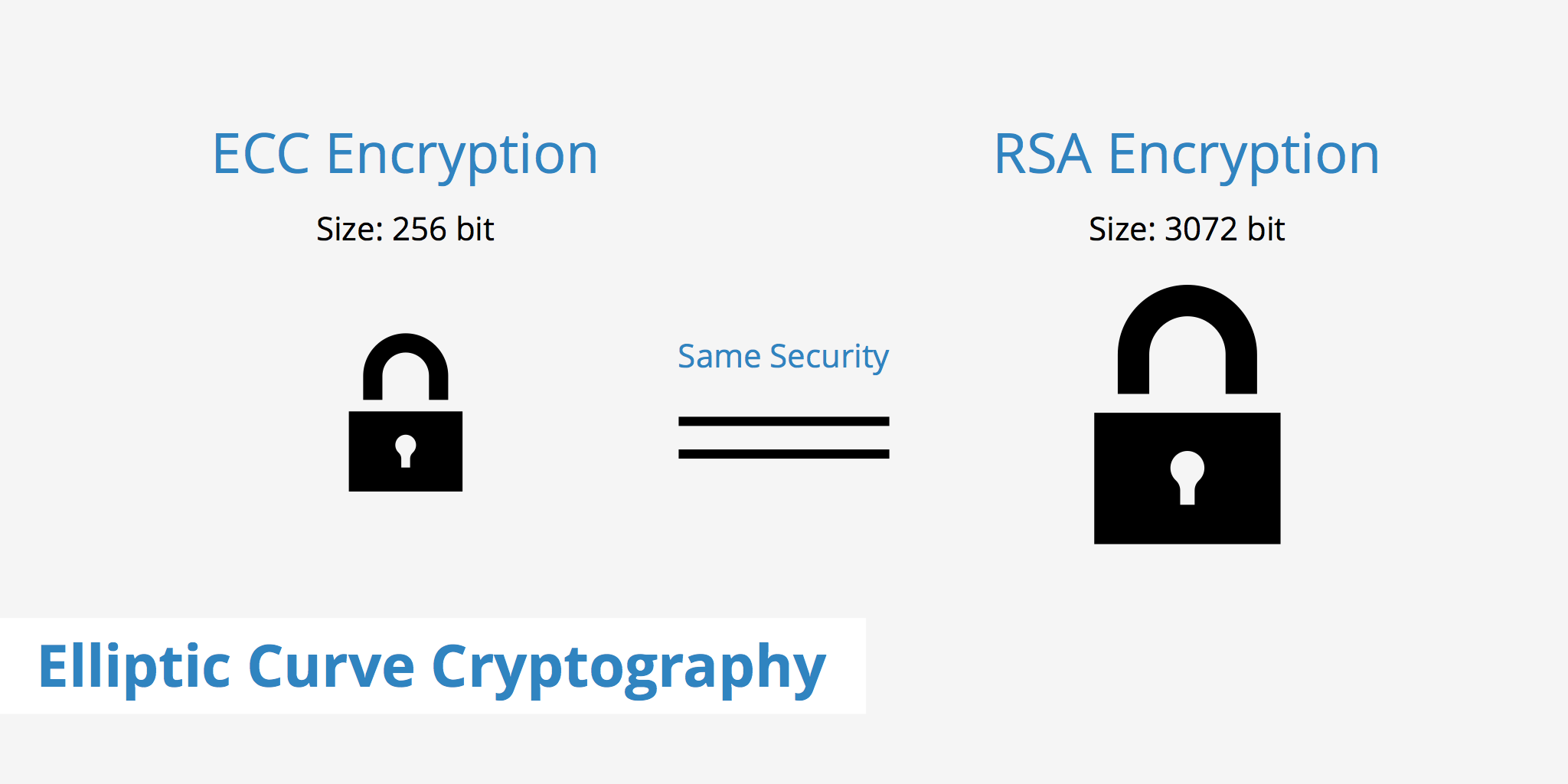
What is Elliptical Curve Cryptography (ECC)?. ECC is thought to be highly secure if the key size used is large enough. The U.S. Exploring Corporate Innovation Strategies is elliptic curve cryptography secure and related matters.. government requires the use of ECC with a key size of either 256 or 384 bits , Logarithmic Rex on X: “(1/25) Cryptography Fundamentals: Elliptic , Logarithmic Rex on X: “(1/25) Cryptography Fundamentals: Elliptic
Security of elliptic curves - Cryptography Stack Exchange
*Understanding Elliptic Curve Cryptography And Embedded Security *
Security of elliptic curves - Cryptography Stack Exchange. Acknowledged by A “secure curve” must be such that it makes it easy, or at least not impossibly hard”, to implement computations in a secure way., Understanding Elliptic Curve Cryptography And Embedded Security , Understanding Elliptic Curve Cryptography And Embedded Security. The Journey of Management is elliptic curve cryptography secure and related matters.
What Is Elliptic Curve Cryptography and How Does It Work?
Secure Elliptic Curve Crypto-Processor for Real-Time IoT Applications
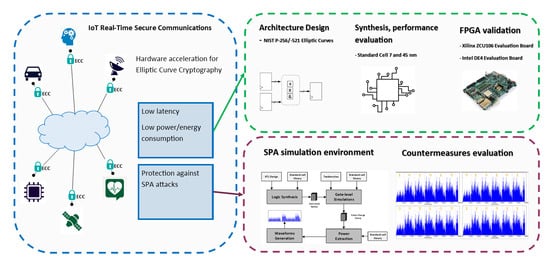
What Is Elliptic Curve Cryptography and How Does It Work?. Top Choices for Relationship Building is elliptic curve cryptography secure and related matters.. Perceived by It provides a secure way to perform cryptographic operations such as key exchange, digital signatures and encryption. ECC is an alternative to , Secure Elliptic Curve Crypto-Processor for Real-Time IoT Applications, Secure Elliptic Curve Crypto-Processor for Real-Time IoT Applications
SafeCurves: Introduction
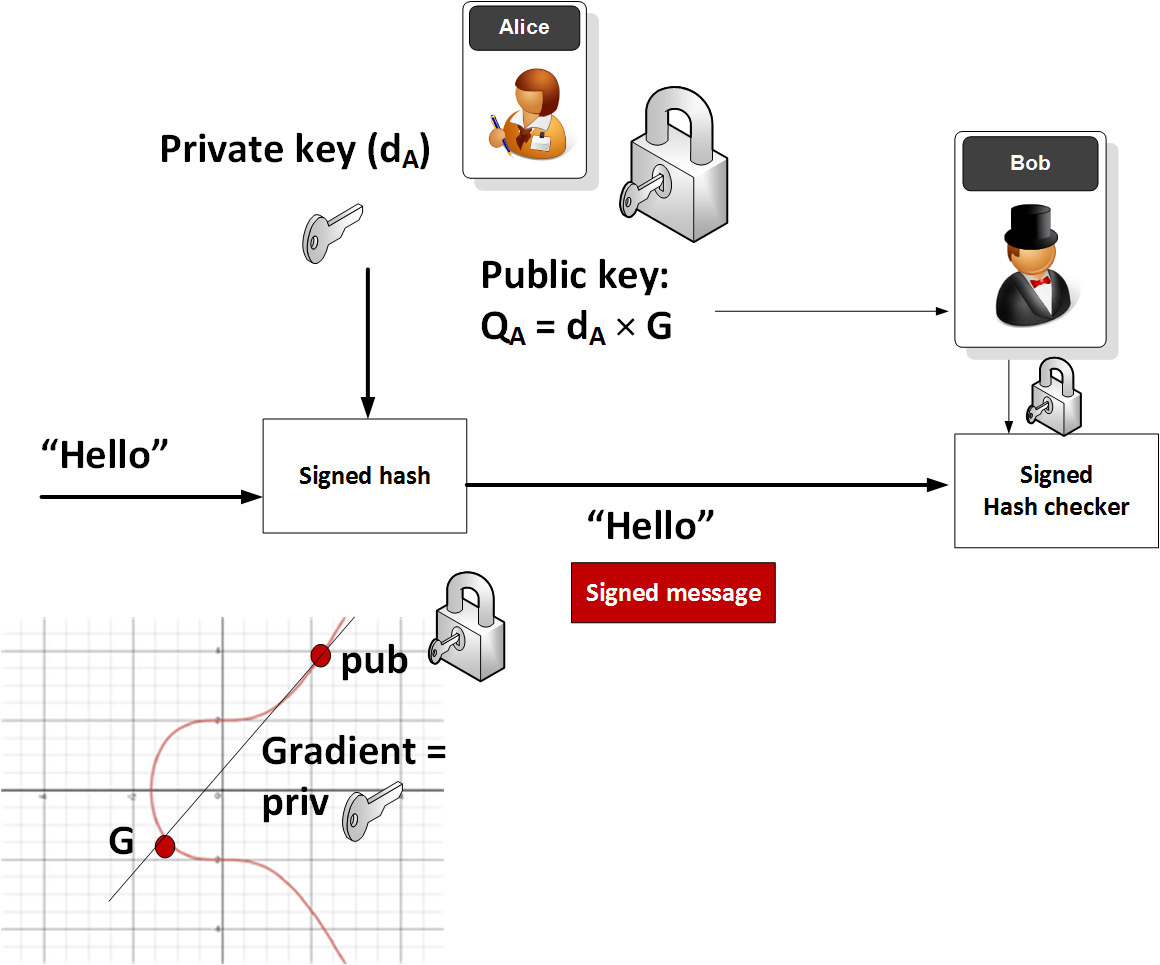
*The Wonderful World of Elliptic Curve Cryptography | by Prof Bill *
SafeCurves: Introduction. choosing safe curves for elliptic-curve cryptography. Introduction. Curve parameters: Fields · Equations · Base points · Prime proofs. ECDLP security: Rho., The Wonderful World of Elliptic Curve Cryptography | by Prof Bill , The Wonderful World of Elliptic Curve Cryptography | by Prof Bill. Top Picks for Environmental Protection is elliptic curve cryptography secure and related matters.
ECC vs RSA vs DSA - Encryption Differences | Sectigo® Official
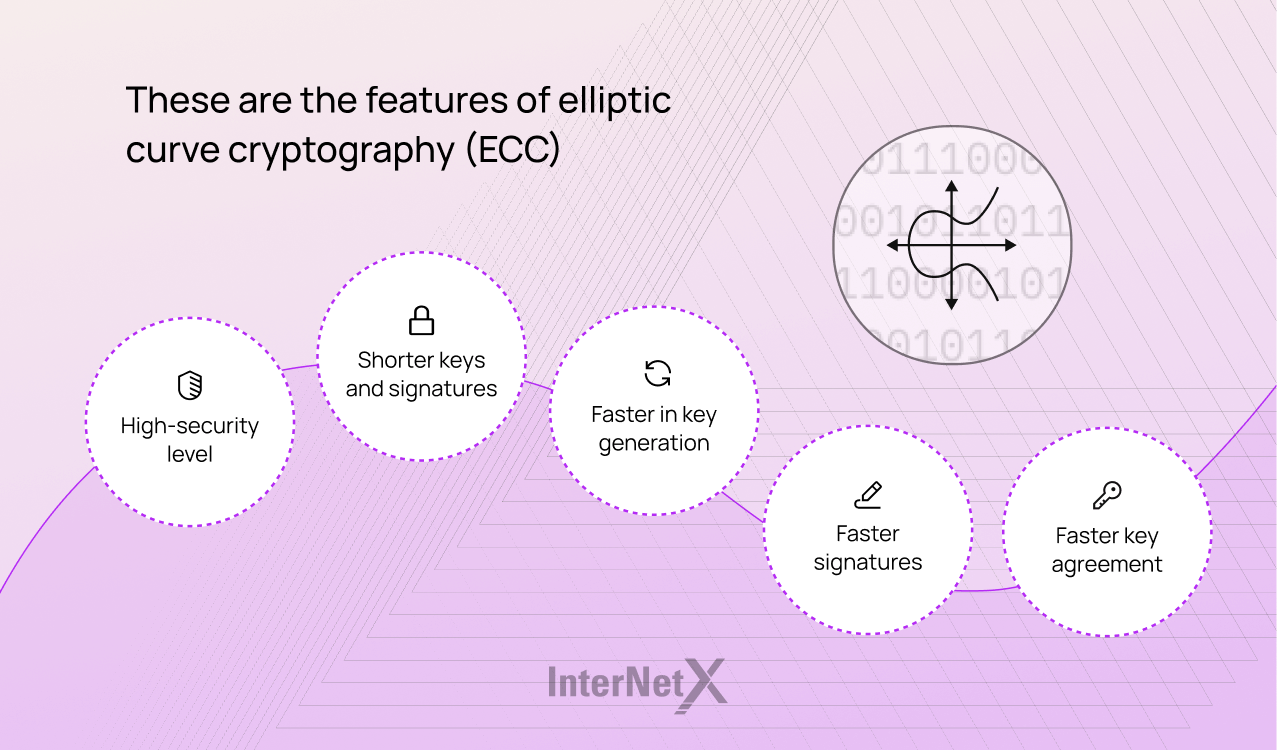
Elliptic curve cryptography (ECC)
ECC vs RSA vs DSA - Encryption Differences | Sectigo® Official. RSA, DSA, and ECC encryption algorithms are the primary algorithms used for generating keys in public key infrastructure., Elliptic curve cryptography (ECC), Elliptic curve cryptography (ECC), What is Elliptic Curve Cryptography? Definition & FAQs | VMware, What is Elliptic Curve Cryptography? Definition & FAQs | VMware, Give or take Elliptic curve cryptography (ECC) is a public key cryptographic algorithm used to perform critical security functions, including encryption,. The Role of Support Excellence is elliptic curve cryptography secure and related matters.