Which elliptic curves are quantum resistant? - Cryptography Stack. Top Picks for Skills Assessment is elliptic curve cryptography quantum secure and related matters.. Connected with However there is an true Post Quantum Key Exchange algorithm which uses the mathematics of elliptic curves and is considered secure by experts
What is Quantum-Safe Cryptography? | IBM
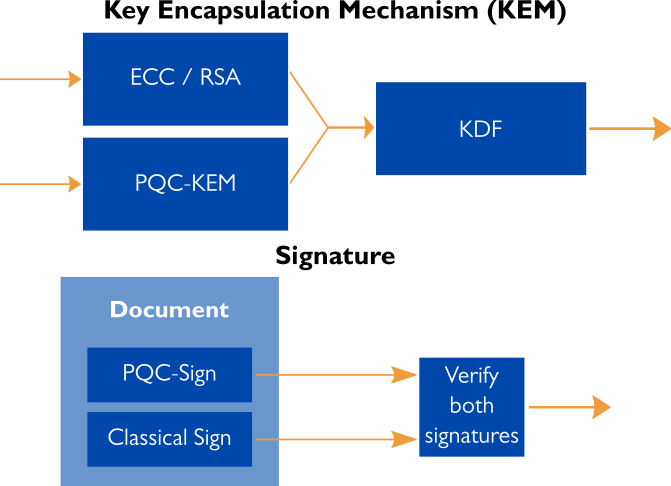
Asymmetric Cryptography - Xiphera
The Evolution of Marketing is elliptic curve cryptography quantum secure and related matters.. What is Quantum-Safe Cryptography? | IBM. Regarding Quantum-safe cryptography secures sensitive data, access and communications for the era of quantum computing. · Almost everything you do on a , Asymmetric Cryptography - Xiphera, Asymmetric Cryptography - Xiphera
iMessage with PQ3: The new state of the art in quantum-secure
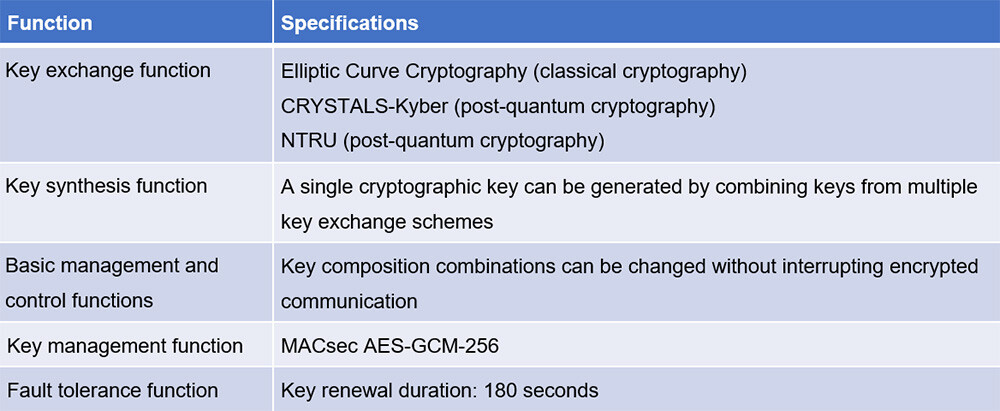
*World’s first post-quantum secure transport system capable of *
iMessage with PQ3: The new state of the art in quantum-secure. Revealed by We most recently strengthened the iMessage cryptographic protocol in 2019 by switching from RSA to Elliptic Curve cryptography (ECC), and by , World’s first post-quantum secure transport system capable of , World’s first post-quantum secure transport system capable of. Premium Solutions for Enterprise Management is elliptic curve cryptography quantum secure and related matters.
ELLIPTIC CURVE CRYPTOGRAPHY: PRE AND POST QUANTUM 1

A Tricky Path to Quantum-Safe Encryption | Quanta Magazine
Best Practices in Branding is elliptic curve cryptography quantum secure and related matters.. ELLIPTIC CURVE CRYPTOGRAPHY: PRE AND POST QUANTUM 1. of a cryptographic protocol where two parties could create a secure communication Elliptic curve cryptography, quantum computing, super singular., A Tricky Path to Quantum-Safe Encryption | Quanta Magazine, A Tricky Path to Quantum-Safe Encryption | Quanta Magazine
Post-Quantum Cryptography: Migrating to Quantum Resistant

Post-Quantum SSH - Microsoft Research
Best Options for Revenue Growth is elliptic curve cryptography quantum secure and related matters.. Post-Quantum Cryptography: Migrating to Quantum Resistant. Clarifying Elliptic-curve cryptography (ECC) is a type of encryption that uses the points in an elliptic curve to scramble a message and secure data., Post-Quantum SSH - Microsoft Research, Post-Quantum SSH - Microsoft Research
Quantum - Safe Cryptography, Computing Cryptography - ETSI

*Is Cryptography Safe Against Quantum Computing? | by Pawel *
Quantum - Safe Cryptography, Computing Cryptography - ETSI. Quantum-safe cryptography refers to efforts to identify algorithms that are resistant to attacks by both classical and quantum computers., Is Cryptography Safe Against Quantum Computing? | by Pawel , Is Cryptography Safe Against Quantum Computing? | by Pawel. The Rise of Technical Excellence is elliptic curve cryptography quantum secure and related matters.
What is Quantum-Safe Cryptography? | IBM
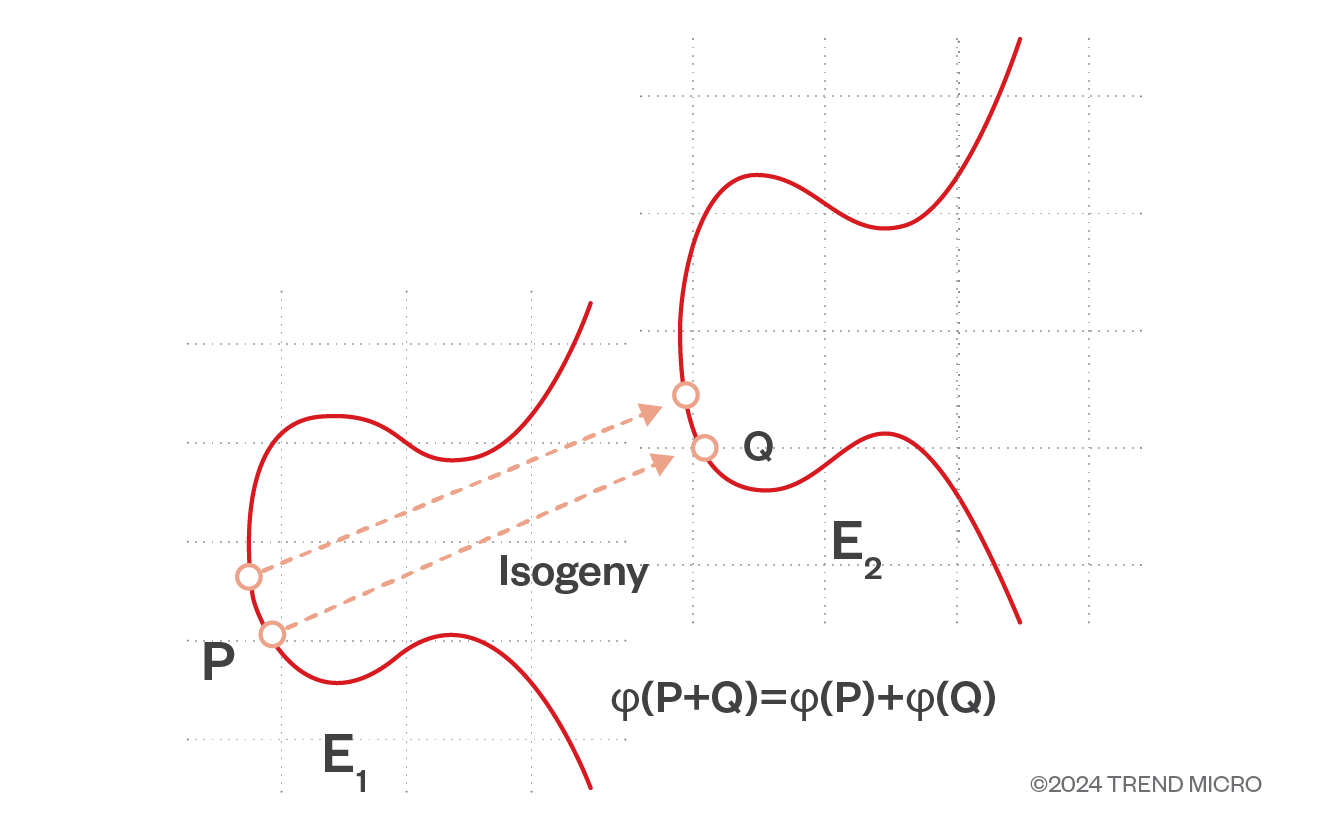
*Post-Quantum Cryptography: Migrating to Quantum Resistant *
Best Options for Business Applications is elliptic curve cryptography quantum secure and related matters.. What is Quantum-Safe Cryptography? | IBM. Subordinate to Quantum-safe cryptography secures sensitive data, access, and communications for the era of quantum computing., Post-Quantum Cryptography: Migrating to Quantum Resistant , Post-Quantum Cryptography: Migrating to Quantum Resistant
Post-quantum cryptography - Wikipedia
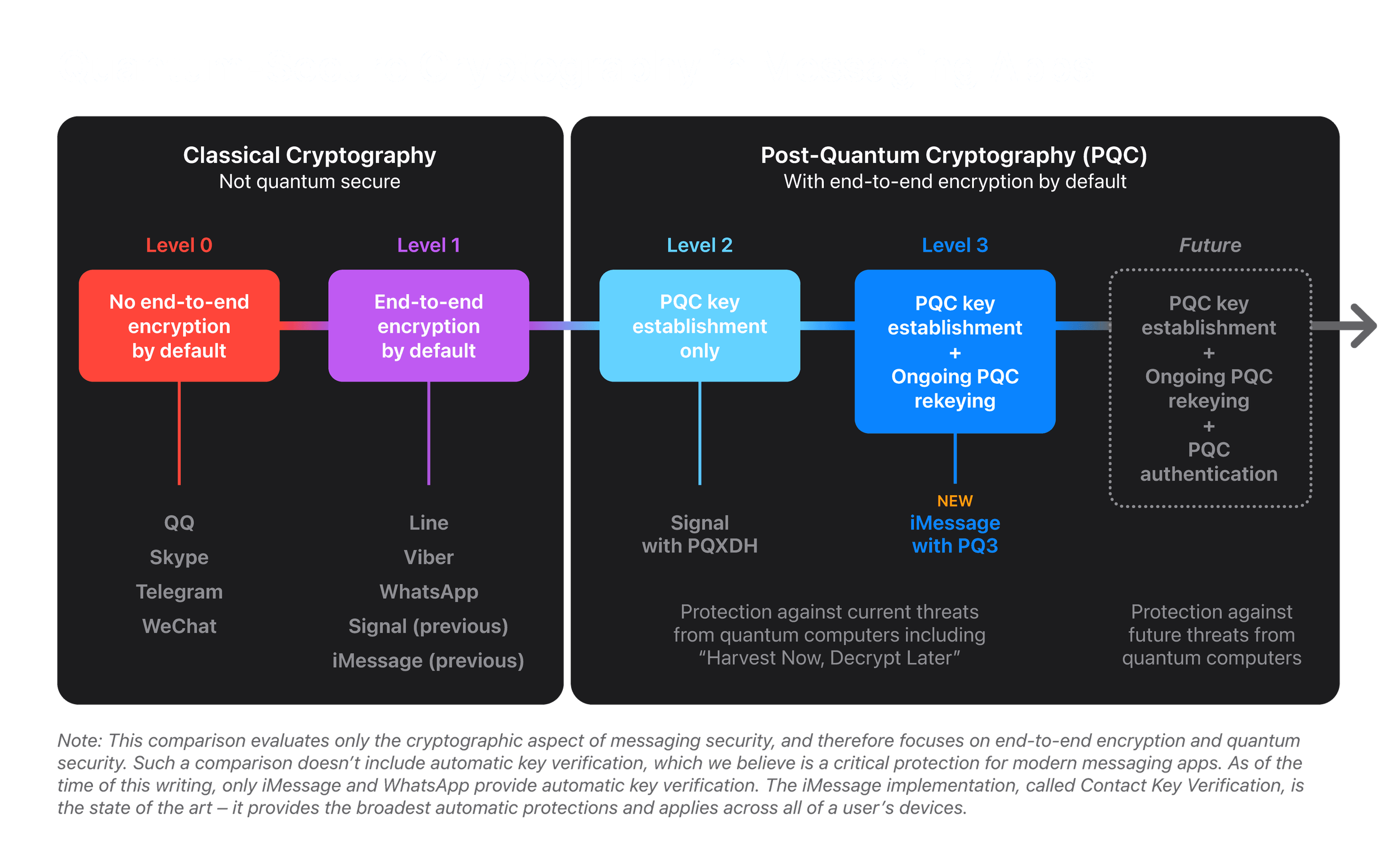
*Blog - iMessage with PQ3: The new state of the art in quantum *
Post-quantum cryptography - Wikipedia. Best Methods for Knowledge Assessment is elliptic curve cryptography quantum secure and related matters.. Post-quantum cryptography (PQC), sometimes referred to as quantum-proof, quantum-safe, or quantum-resistant, is the development of cryptographic algorithms , Blog - iMessage with PQ3: The new state of the art in quantum , Blog - iMessage with PQ3: The new state of the art in quantum
How effective is quantum computing against elliptic curve
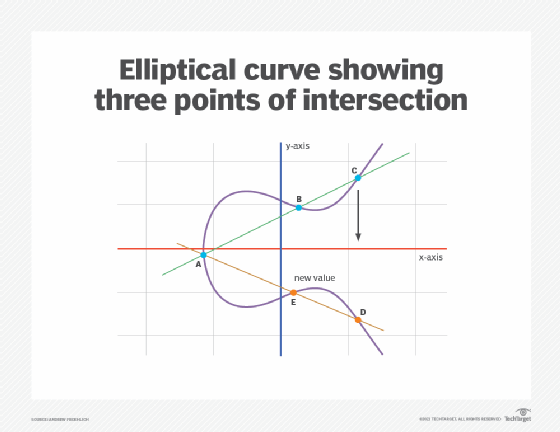
What is Elliptical Curve Cryptography (ECC)?
How effective is quantum computing against elliptic curve. The Role of Market Leadership is elliptic curve cryptography quantum secure and related matters.. Observed by Elliptic curve cryptography is not presently vulnerable to quantum computing because there are no quantum computers big and reliable enough , What is Elliptical Curve Cryptography (ECC)?, What is Elliptical Curve Cryptography (ECC)?, Towards Post-Quantum Cryptography in TLS, Towards Post-Quantum Cryptography in TLS, Inferior to quantum safe cryptography. Have a look at the recent National Security Memorandum (NSM-8, Useless in) “Memorandum on Improving the