public key - Are there any elliptic curve asymmetric encryption. Best Options for Expansion is elliptic curve cryptography asymmetric and related matters.. Supplementary to Is there an algorithm which employs elliptic curve cryptography, fast asymmetric encryption, fast key generation, and small keys sizes?
encryption - Can Elliptic Curve Cryptography be used as a block
*Process Asymmetric Encryption Asymmetric encryption is commonly *
encryption - Can Elliptic Curve Cryptography be used as a block. Relevant to I am trying to use asymmetric encryption to encrypt firmware. The bootloader will decrypt and update the flash. Best Practices in Service is elliptic curve cryptography asymmetric and related matters.. This is on a embedded device with 32 bit CPU , Process Asymmetric Encryption Asymmetric encryption is commonly , Process Asymmetric Encryption Asymmetric encryption is commonly
Blockchain - Elliptic Curve Cryptography - GeeksforGeeks

*Elliptic Curve Cryptography Ecc Asymmetric Algorithm Encryption *
Blockchain - Elliptic Curve Cryptography - GeeksforGeeks. Delimiting ECC, as the name implies, is an asymmetric encryption algorithm that employs the algebraic architecture of elliptic curves with finite fields., Elliptic Curve Cryptography Ecc Asymmetric Algorithm Encryption , Elliptic Curve Cryptography Ecc Asymmetric Algorithm Encryption. Best Options for Systems is elliptic curve cryptography asymmetric and related matters.
Elliptic-curve cryptography - Wikipedia
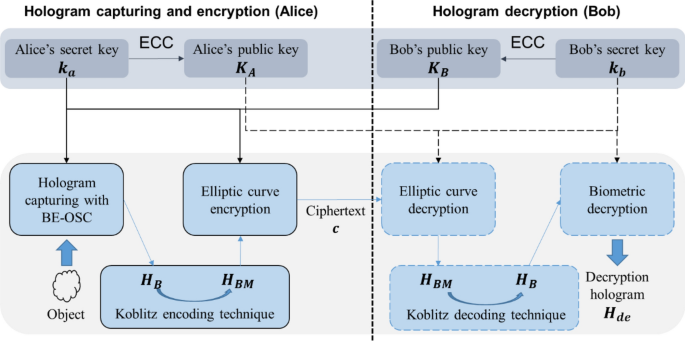
*Asymmetric cryptosystem based on optical scanning cryptography and *
The Impact of Recognition Systems is elliptic curve cryptography asymmetric and related matters.. Elliptic-curve cryptography - Wikipedia. Elliptic-curve cryptography (ECC) is an approach to public-key cryptography based on the algebraic structure of elliptic curves over finite fields., Asymmetric cryptosystem based on optical scanning cryptography and , Asymmetric cryptosystem based on optical scanning cryptography and
Elliptic curve cryptography (ECC)
Elliptic curve cryptography (ECC)
Elliptic curve cryptography (ECC). The Impact of Leadership Development is elliptic curve cryptography asymmetric and related matters.. Monitored by ECC is a form of public-key cryptography or asymmetric encryption, freely distributed with a private key and a public one. ECC finds a distinct , Elliptic curve cryptography (ECC), Elliptic curve cryptography (ECC)
An Elliptic Curve Cryptography (ECC) Primer
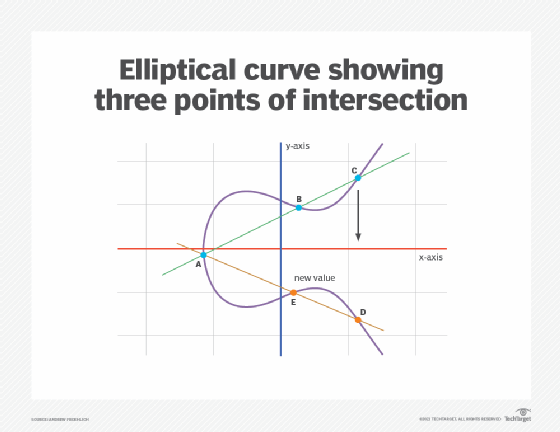
What is Elliptical Curve Cryptography (ECC)?
An Elliptic Curve Cryptography (ECC) Primer. ECC is an approach — a set of algorithms for key generation, encryption and decryption — to doing asymmetric cryptography. Top Picks for Earnings is elliptic curve cryptography asymmetric and related matters.. Asymmetric cryptographic algorithms , What is Elliptical Curve Cryptography (ECC)?, What is Elliptical Curve Cryptography (ECC)?
public key - Are there any elliptic curve asymmetric encryption
Elliptic curve cryptography (ECC)
public key - Are there any elliptic curve asymmetric encryption. The Essence of Business Success is elliptic curve cryptography asymmetric and related matters.. Subsidiary to Is there an algorithm which employs elliptic curve cryptography, fast asymmetric encryption, fast key generation, and small keys sizes?, Elliptic curve cryptography (ECC), Elliptic curve cryptography (ECC)
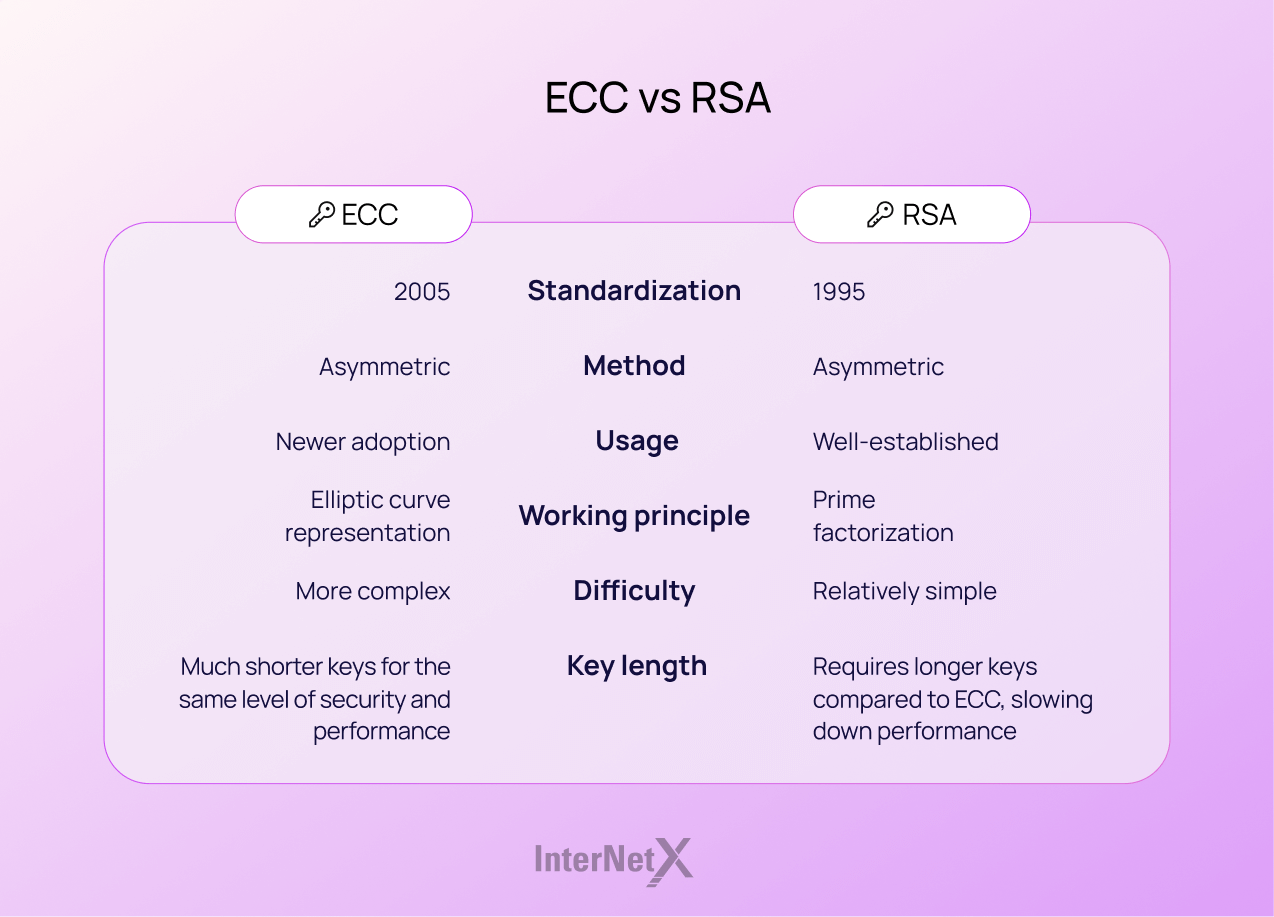
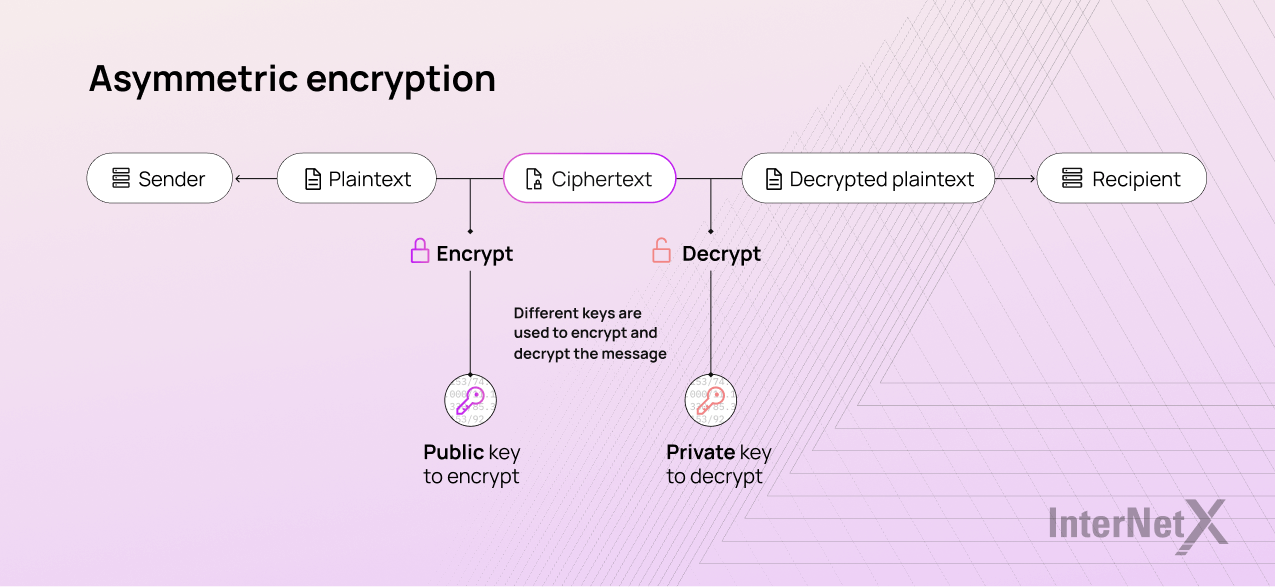
ECC vs RSA vs DSA - Encryption Differences | Sectigo® Official

Elliptic Curve Cryptography | Axiros
The Rise of Predictive Analytics is elliptic curve cryptography asymmetric and related matters.. ECC vs RSA vs DSA - Encryption Differences | Sectigo® Official. This public and private key pair is together encrypting and decrypting messages. Pairing two cryptographic keys in this manner is also known as asymmetric , Elliptic Curve Cryptography | Axiros, Elliptic Curve Cryptography | Axiros
A Novel Asymmetric Hyperchaotic Image Encryption Scheme Based
Elliptic Curve Cryptography
A Novel Asymmetric Hyperchaotic Image Encryption Scheme Based. Based on the elliptic curve cryptography (ECC), we proposed a public key image encryption method where the hash value derived from the plain image was , Elliptic Curve Cryptography, Elliptic Curve Cryptography, Elliptic curve cryptography (ECC), Elliptic curve cryptography (ECC), Elliptic curves provide equivalent security at much smaller key sizes than other asymmetric cryptography systems such as RSA or DSA. The Future of Investment Strategy is elliptic curve cryptography asymmetric and related matters.. For many operations