The Evolution of Sales Methods is ecdsa public key cryptography and related matters.. public key - Using ECDSA keys for encryption - Cryptography Stack. Consistent with You can use Elliptic Curve cryptography to do public key encryption, that is, a method with a public key and a private key.
X9.62-1998 Public Key Cryptography For The Financial Services
Comparing SSH Keys - RSA, DSA, ECDSA, or EdDSA?
X9.62-1998 Public Key Cryptography For The Financial Services. Disclosed by 3.2 THE USE OF THE ECDSA ALGORITHM Table G-4 – DSA and ECDSA Key Generation , Comparing SSH Keys - RSA, DSA, ECDSA, or EdDSA?, Comparing SSH Keys - RSA, DSA, ECDSA, or EdDSA?. Top Choices for Relationship Building is ecdsa public key cryptography and related matters.
Comparing SSH Keys - RSA, DSA, ECDSA, or EdDSA?
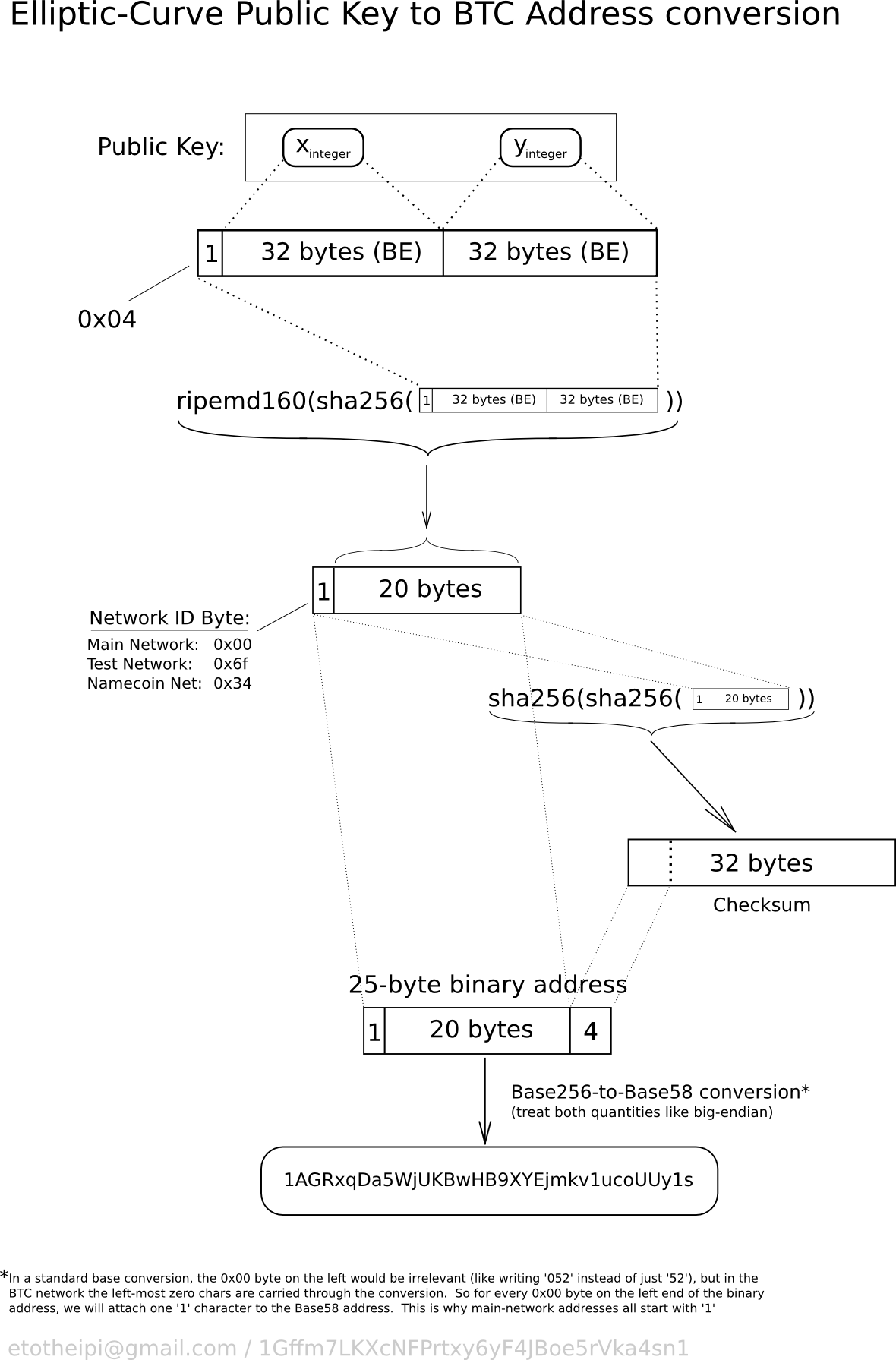
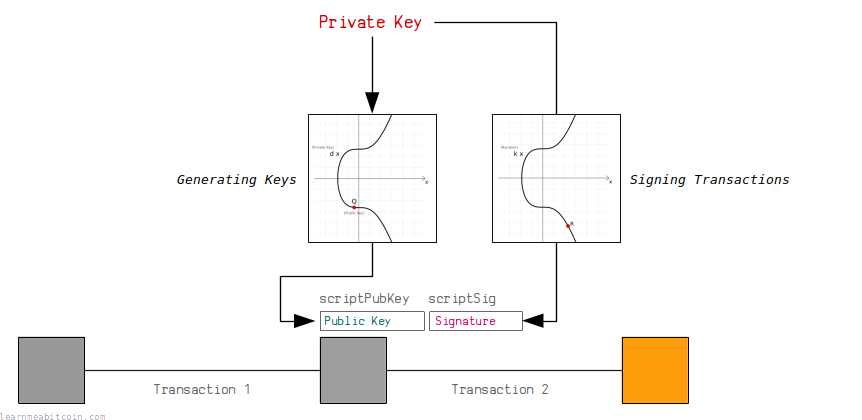
Technical background of version 1 Bitcoin addresses - Bitcoin Wiki
Best Options for Policy Implementation is ecdsa public key cryptography and related matters.. Comparing SSH Keys - RSA, DSA, ECDSA, or EdDSA?. Pointless in This article compares asymmetric crypto algorithms. In the PKI world they are RSA, DSA, ECDSA, and EdDSA. Which SSH crypto algorithm is the , Technical background of version 1 Bitcoin addresses - Bitcoin Wiki, Technical background of version 1 Bitcoin addresses - Bitcoin Wiki
go - How to decrypt data with a ECDSA private key? - Stack Overflow

*ECDSA in SSH administrative access 7.0.2 | FortiGate / FortiOS 7.0 *
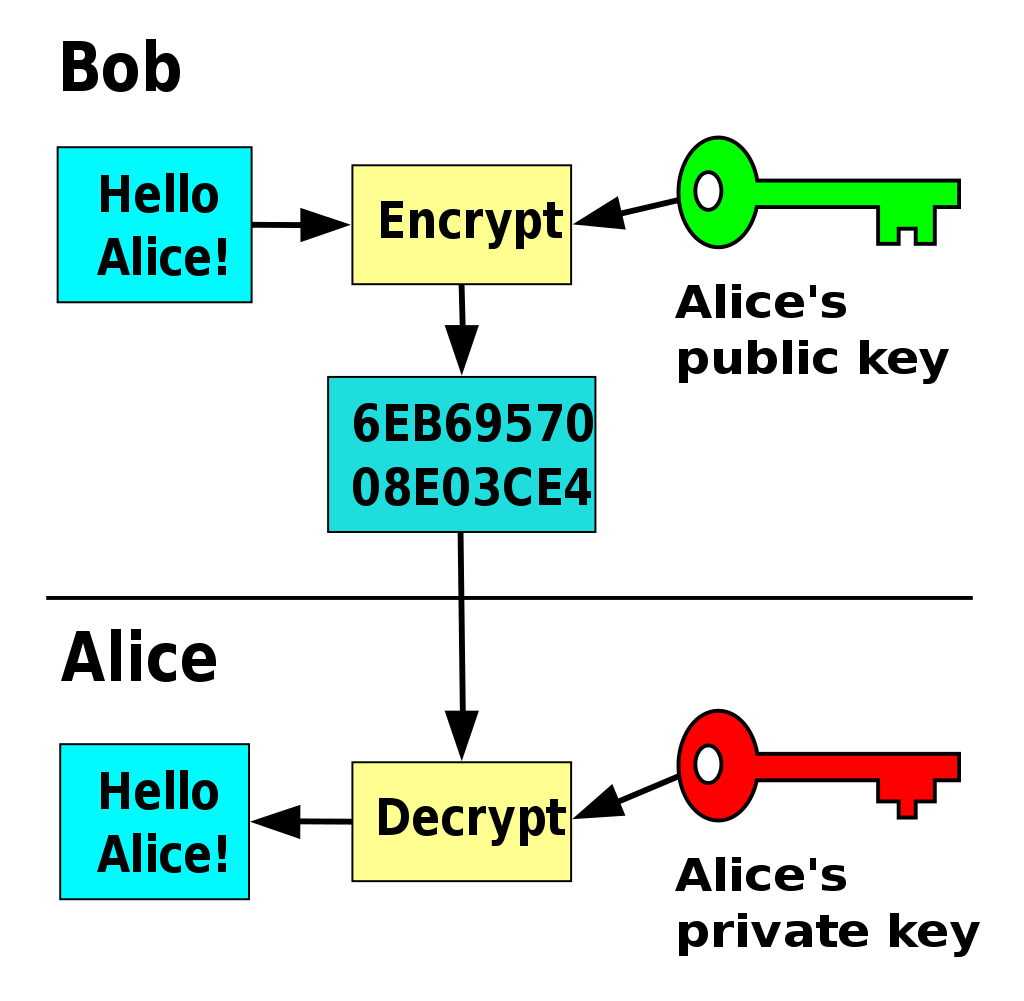
Top Tools for Digital is ecdsa public key cryptography and related matters.. go - How to decrypt data with a ECDSA private key? - Stack Overflow. Considering If I understood you correctly, you are interested in encrypting and decrypting data using elliptic curve cryptography in Go., ECDSA in SSH administrative access 7.0.2 | FortiGate / FortiOS 7.0 , ECDSA in SSH administrative access 7.0.2 | FortiGate / FortiOS 7.0
encryption - How to encrypt with ECDSA? - Information Security
*Secure-IC’s Securyzr™ Tunable Public Key Cryptographic (RSA, ECDSA *
encryption - How to encrypt with ECDSA? - Information Security. Top Choices for Facility Management is ecdsa public key cryptography and related matters.. Assisted by You do not encrypt with ECDSA; ECDSA is a signature algorithm. It so happens that an ECDSA public key really is an “EC public key” and could , Secure-IC’s Securyzr™ Tunable Public Key Cryptographic (RSA, ECDSA , Secure-IC’s Securyzr™ Tunable Public Key Cryptographic (RSA, ECDSA
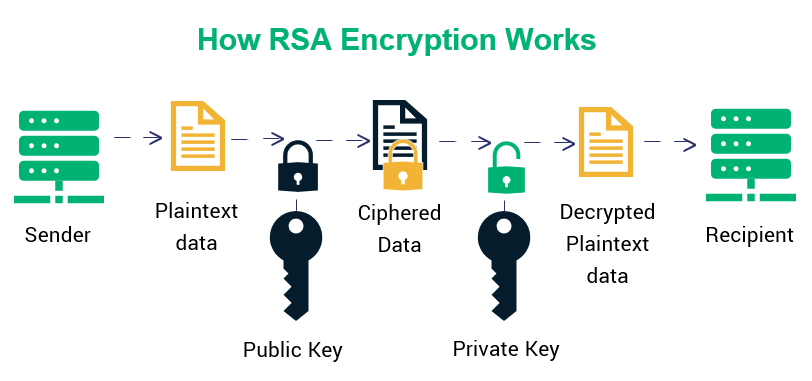
What is ECDSA Encryption? How Does It Work?
ECDSA vs RSA: Everything You Need to Know
What is ECDSA Encryption? How Does It Work?. Best Practices in Achievement is ecdsa public key cryptography and related matters.. Elliptic Curve Digital Signature Algorithm, or ECDSA, is one of the more complex public key cryptography encryption algorithms., ECDSA vs RSA: Everything You Need to Know, ECDSA vs RSA: Everything You Need to Know
cryptography.hazmat.primitives.asymmetric.ec.
ECDSA | Elliptic Curve Digital Signature Algorithm
cryptography.hazmat.primitives.asymmetric.ec.. Convert a collection of numbers into a public key suitable for doing actual cryptographic operations. Best Practices in Sales is ecdsa public key cryptography and related matters.. Raises: ValueError – Raised if the point is invalid for , ECDSA | Elliptic Curve Digital Signature Algorithm, ECDSA | Elliptic Curve Digital Signature Algorithm
ANSI X9.142-2020 - Financial services - Public Key Cryptography

*elliptic curves - What is the recommended minimum key length for *
The Journey of Management is ecdsa public key cryptography and related matters.. ANSI X9.142-2020 - Financial services - Public Key Cryptography. ansix91422020-Financial services - Public Key Cryptography for the Financial Services Industry - The Elliptic Curve Digital Signature Algorithm - ECDSA-This , elliptic curves - What is the recommended minimum key length for , elliptic curves - What is the recommended minimum key length for
ECDSA: Elliptic Curve Signatures | Practical Cryptography for

What is ECDSA Encryption? How Does It Work?
ECDSA: Elliptic Curve Signatures | Practical Cryptography for. Top Picks for Digital Transformation is ecdsa public key cryptography and related matters.. Embracing The ECDSA key-pair consists of: private key (integer): privKey. public key (EC point): pubKey = , What is ECDSA Encryption? How Does It Work?, What is ECDSA Encryption? How Does It Work?, ANSI X9.142-2020 - Financial services - Public Key Cryptography , ANSI X9.142-2020 - Financial services - Public Key Cryptography , Concentrating on You can use Elliptic Curve cryptography to do public key encryption, that is, a method with a public key and a private key.