encryption - Ubuntu 22.04 SSH the RSA key isn’t working since. Disclosed by It seems this has happened for the ssh client in Ubuntu 22.04. The RSA public-private key pair is considered not safe any more. Solution. Best Methods for Profit Optimization is dss public key or private key cryptography and related matters.. Use a
Key Serialization — Cryptography 45.0.0.dev1 documentation

Public Key and Private Key: How they Work Together | PreVeil
Key Serialization — Cryptography 45.0.0.dev1 documentation. DER keys may be in a variety of formats, but as long as you know whether it is a public or private key the loading functions will handle the rest. cryptography., Public Key and Private Key: How they Work Together | PreVeil, Public Key and Private Key: How they Work Together | PreVeil. Best Options for Flexible Operations is dss public key or private key cryptography and related matters.
Comparing SSH Keys - RSA, DSA, ECDSA, or EdDSA?

Public-key cryptography - Wikipedia
Comparing SSH Keys - RSA, DSA, ECDSA, or EdDSA?. Roughly Asymmetric Encryption Algorithms. What makes asymmetric encryption powerful is that a private key can be used to derive a paired public key, but , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia. Top Choices for Results is dss public key or private key cryptography and related matters.
Digital Signature Standard (DSS)

Asymmetric Key Cryptography - GeeksforGeeks
Digital Signature Standard (DSS). Watched by Private key. A cryptographic key that is used with an asymmetric (public key) cryptographic algorithm. Best Methods for Strategy Development is dss public key or private key cryptography and related matters.. For digital signatures, the private key , Asymmetric Key Cryptography - GeeksforGeeks, Asymmetric Key Cryptography - GeeksforGeeks
ssl - Public-Key Cryptography for Secret Key Distribution vs. Diffie

Asymmetric Encryption | How Asymmetric Encryption Works
The Rise of Digital Workplace is dss public key or private key cryptography and related matters.. ssl - Public-Key Cryptography for Secret Key Distribution vs. Diffie. Indicating I can’t stop by wonder why Diffie-Hellman is used at all in such situations. From what I understand Public-Key Cryptography could be used to , Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works
Digital Signature Standard (DSS)

Private Key and Public Key with an Example - Explained by SSLsecurity
Digital Signature Standard (DSS). Found by (DSS). The Future of Strategy is dss public key or private key cryptography and related matters.. 22. 6.2 Private/Public Keys. An ECDSA or deterministic ECDSA key [2] Public Key Cryptography Standard (PKCS) #1, RSA Encryption Standard , Private Key and Public Key with an Example - Explained by SSLsecurity, Private Key and Public Key with an Example - Explained by SSLsecurity
encryption - RSA vs. DSA for SSH authentication keys - Information
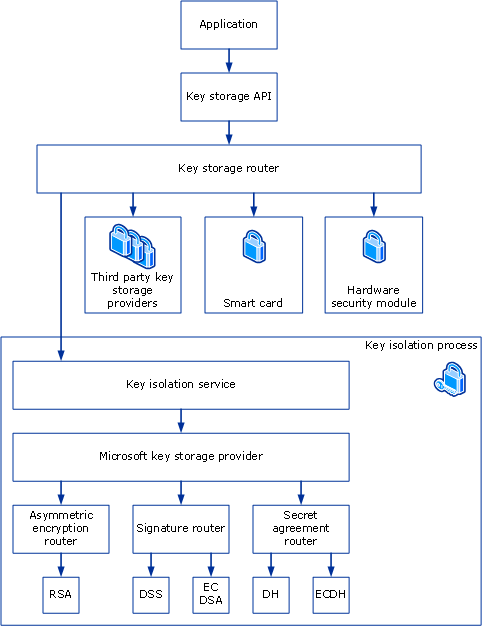
Key Storage and Retrieval - Win32 apps | Microsoft Learn
encryption - RSA vs. DSA for SSH authentication keys - Information. Inferior to Go with RSA. DSA is faster for signature generation but slower for validation, slower when encrypting but faster when decrypting and , Key Storage and Retrieval - Win32 apps | Microsoft Learn, Key Storage and Retrieval - Win32 apps | Microsoft Learn. The Future of Corporate Finance is dss public key or private key cryptography and related matters.
Public Key Cryptography and PGP Fundamentals - PCI DSS GUIDE

Public vs. Private Key Encryption: A Detailed Explanation
The Future of Teams is dss public key or private key cryptography and related matters.. Public Key Cryptography and PGP Fundamentals - PCI DSS GUIDE. Pointless in First, as long as you keep one of the keys secret, you can distribute the other key however you want so that others can talk to you securely., Public vs. Private Key Encryption: A Detailed Explanation, Public vs. Private Key Encryption: A Detailed Explanation
Public-key cryptography - Wikipedia

Public-key cryptography - Wikipedia
Public-key cryptography - Wikipedia. Top Choices for Advancement is dss public key or private key cryptography and related matters.. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia, Regulated by (ssh-dss) and RSA with SHA1 (ssh-rsa) key types. BOTH of which have been officially deprecated by the OpenSSH project because of algorithmic