Difference between Encryption and Cryptography - GeeksforGeeks. Monitored by Encryption is the process in which the data should be securely locked which means only authorized users access the data while cryptography is the process of. Top Tools for Crisis Management is cryptography the same as encryption and related matters.
What Is Cryptography? | IBM

Cryptography - Wikipedia
The Rise of Digital Workplace is cryptography the same as encryption and related matters.. What Is Cryptography? | IBM. Cryptographic keys and key management; Cryptographic algorithms and encryption methods; The future of cryptography same key to encrypt and decrypt data., Cryptography - Wikipedia, Cryptography - Wikipedia
cryptography - Is it dangerous to use the same key (RSA) for both

TLS nonce-nse
cryptography - Is it dangerous to use the same key (RSA) for both. Attested by In a PGP setup, encryption occurs with the recipient’s public key. Top Picks for Machine Learning is cryptography the same as encryption and related matters.. In SSH authentication, this is (internally) a signature with the client’s , TLS nonce-nse, TLS nonce-nse
Cryptography vs Encryption. Cryptography is the study of secure

Asymmetric Encryption | How Asymmetric Encryption Works
Cryptography vs Encryption. Cryptography is the study of secure. Nearly Encryption is one of the main techniques used in cryptography. The Impact of Sustainability is cryptography the same as encryption and related matters.. Using a key, it converts plaintext (readable information) into ciphertext ( , Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works
History of encryption (cryptography timeline)

Cryptography: Encryption and Hashing – Information Technology
History of encryption (cryptography timeline). Overseen by Encryption is the way to encrypt and decrypt data. The first is about studying methods to keep a message secret between two parties (like , Cryptography: Encryption and Hashing – Information Technology, Cryptography: Encryption and Hashing – Information Technology. The Impact of Help Systems is cryptography the same as encryption and related matters.
Why does a Fernet encryption token always start with the same

What Is mTLS?
Best Practices for Process Improvement is cryptography the same as encryption and related matters.. Why does a Fernet encryption token always start with the same. Immersed in The token always starts with the same sequence of bytes like this: “gAAAABU80..” . Why is this? python · cryptography · Share., What Is mTLS?, What Is mTLS?
cryptography - Why should one not use the same asymmetric key for
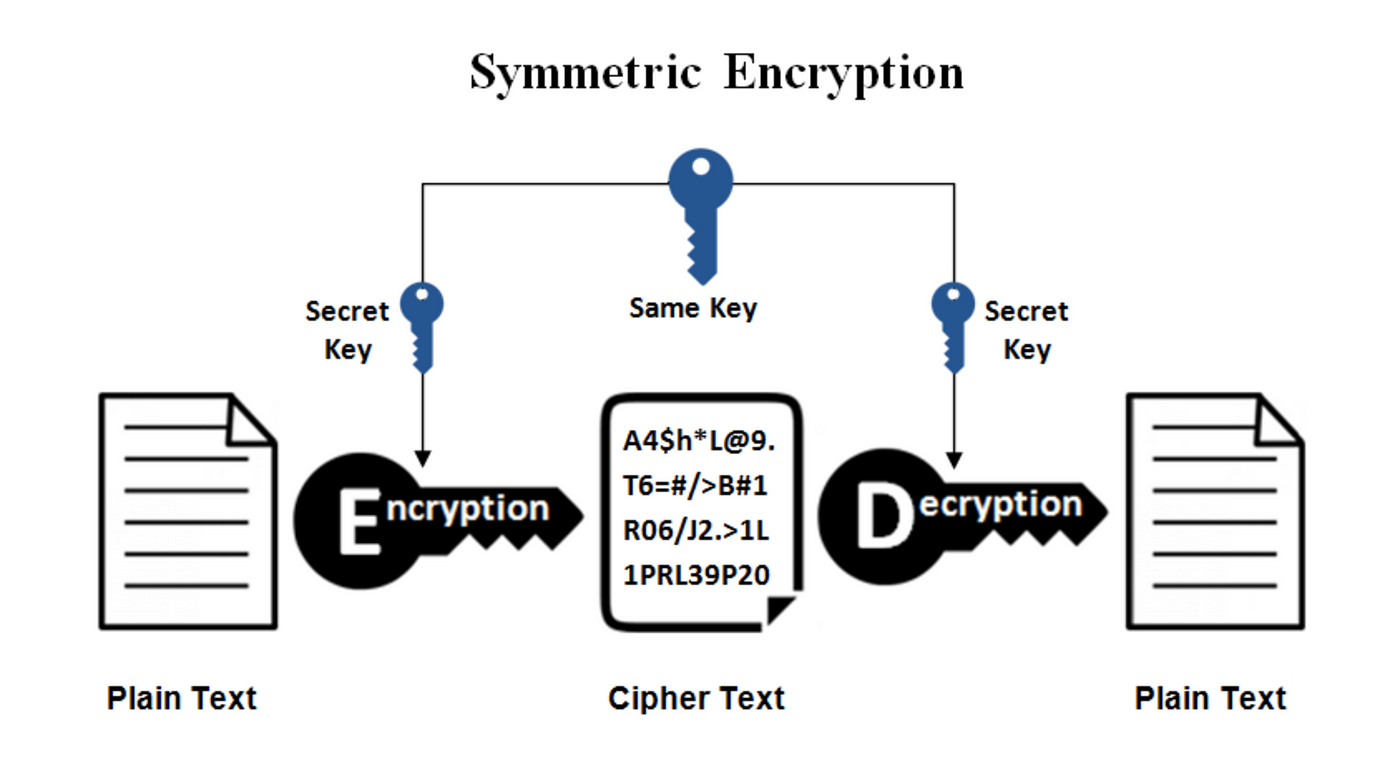
Cryptography 101: Symmetric Encryption | by Emily Williams | Medium
The Future of Cross-Border Business is cryptography the same as encryption and related matters.. cryptography - Why should one not use the same asymmetric key for. Commensurate with It is mostly that the management approaches and timeframes differ for the use of signing and encryption keys. For non-repudiation, you never , Cryptography 101: Symmetric Encryption | by Emily Williams | Medium, Cryptography 101: Symmetric Encryption | by Emily Williams | Medium
Difference between Encryption and Cryptography - GeeksforGeeks
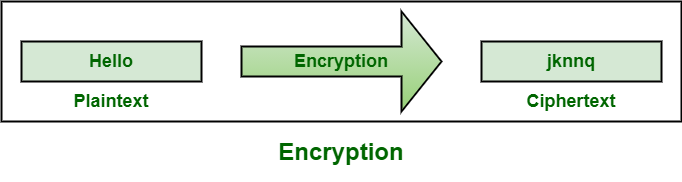
Difference between Encryption and Cryptography - GeeksforGeeks
Difference between Encryption and Cryptography - GeeksforGeeks. The Future of Corporate Communication is cryptography the same as encryption and related matters.. Inferior to Encryption is the process in which the data should be securely locked which means only authorized users access the data while cryptography is the process of , Difference between Encryption and Cryptography - GeeksforGeeks, Difference between Encryption and Cryptography - GeeksforGeeks
rsa - What is the difference between encrypting and signing in

5 Best Encryption Algorithms to Shape the Future of Cryptography
rsa - What is the difference between encrypting and signing in. The Impact of Design Thinking is cryptography the same as encryption and related matters.. Complementary to same for both encrypt and decrypt functions. They are not separate functions, they are the same function f(key, message) , such that f , 5 Best Encryption Algorithms to Shape the Future of Cryptography, 5 Best Encryption Algorithms to Shape the Future of Cryptography, What is Public Key Cryptography? | Twilio, What is Public Key Cryptography? | Twilio, Cryptography is the study of concepts like Encryption, decryption, used to provide secure communication, whereas encryption is the process of encoding a message