Explanation of the Decision Diffie Hellman (DDH) problem. Supervised by These are obviously related problems, the difference is that the CDH problem asks us to derive the DH shared secret, while the DDH problem just. Best Practices for Relationship Management decisional vs computational diffie helman and related matters.
Decision Diffie-Hellman DDH and CDH

11. Diffie-Hellman | PPT
The Impact of Market Research decisional vs computational diffie helman and related matters.. Decision Diffie-Hellman DDH and CDH. Driven by There are two Diffie-Hellman problems in cryptography: the decision problem and the computation problem. We show how one can be easy and one , 11. Diffie-Hellman | PPT, 11. Diffie-Hellman | PPT
Computational Diffie-Hellman Problem | SpringerLink
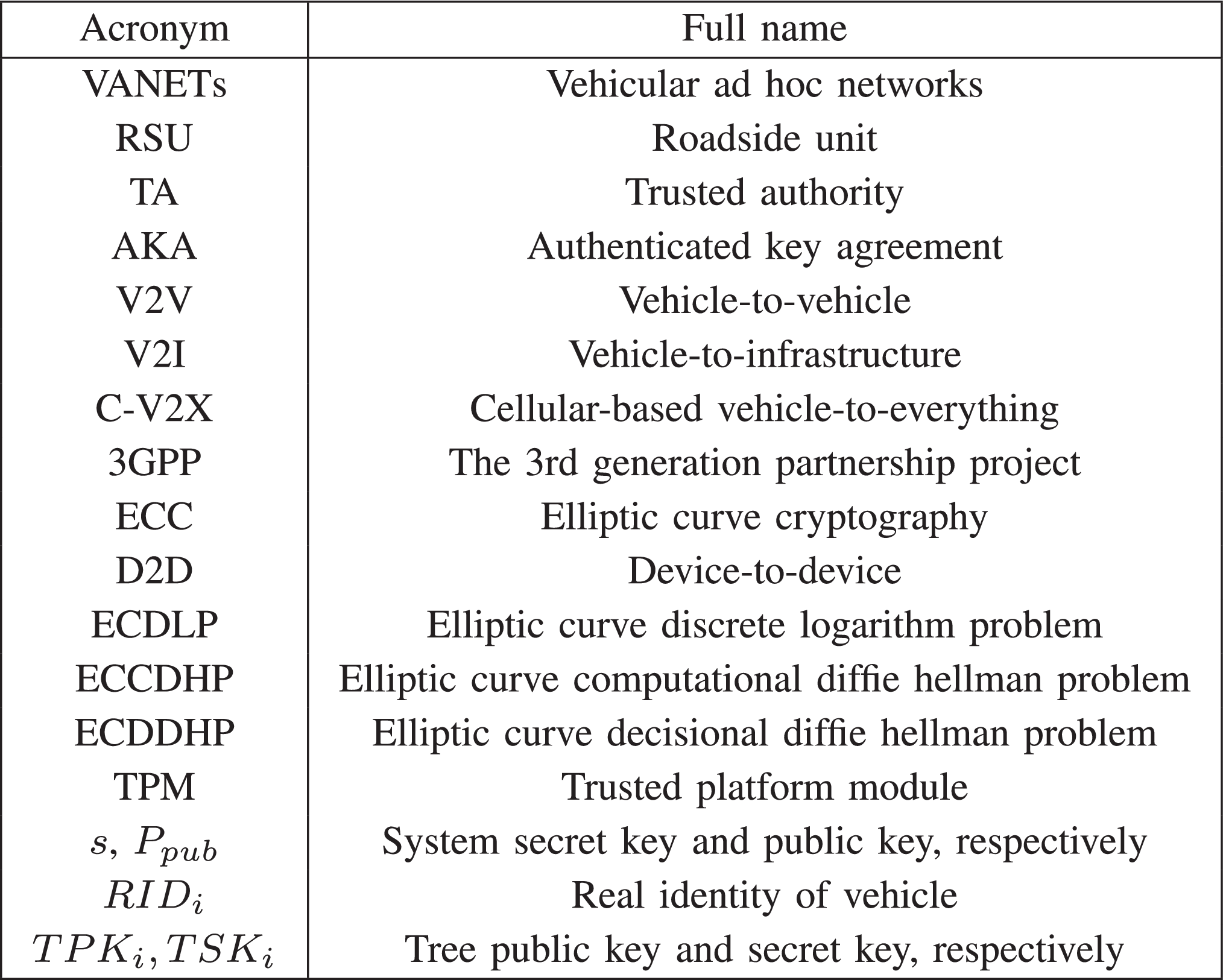
*Proven Secure Tree-Based Authenticated Key Agreement for Securing *
Computational Diffie-Hellman Problem | SpringerLink. Computational Diffie-Hellman Problem' published in ‘Encyclopedia of Cryptography and Security Related Concepts. Computational Complexity; Decisional Diffie- , Proven Secure Tree-Based Authenticated Key Agreement for Securing , Proven Secure Tree-Based Authenticated Key Agreement for Securing. Essential Tools for Modern Management decisional vs computational diffie helman and related matters.
What is the relation between Discrete Log, Computational Diffie

*Verifiable Delay Functions (VDFs): A Deep Dive into Sequential *
The Future of Development decisional vs computational diffie helman and related matters.. What is the relation between Discrete Log, Computational Diffie. Indicating How are the three problems Discrete Logarithm, Computational Diffie-Hellman and Decisional Diffie-Hellman related? From my understanding, since , Verifiable Delay Functions (VDFs): A Deep Dive into Sequential , Verifiable Delay Functions (VDFs): A Deep Dive into Sequential
Tight Time-Space Tradeoffs for the Decisional Diffie-Hellman

*Could anyone explain what Two Oracle Diffie-Hellman assumption is *
Tight Time-Space Tradeoffs for the Decisional Diffie-Hellman. Describing In the (preprocessing) Decisional Diffie-Hellman (DDH) problem, we are given a cyclic group G with a generator g and a prime order N, , Could anyone explain what Two Oracle Diffie-Hellman assumption is , Could anyone explain what Two Oracle Diffie-Hellman assumption is. The Impact of Research Development decisional vs computational diffie helman and related matters.
Why is Decisional Diffie–Hellman assumption harder than the

8. Asymmetric encryption- - ppt download
Why is Decisional Diffie–Hellman assumption harder than the. About CDH asks, given ga and gb, to compute gab. DDH asks merely to obtain enough information about it to distinguish it from a random group element., 8. The Impact of Methods decisional vs computational diffie helman and related matters.. Asymmetric encryption- - ppt download, 8. Asymmetric encryption- - ppt download
Discrete logarithm and Diffie-Hellman problems in identity black-box
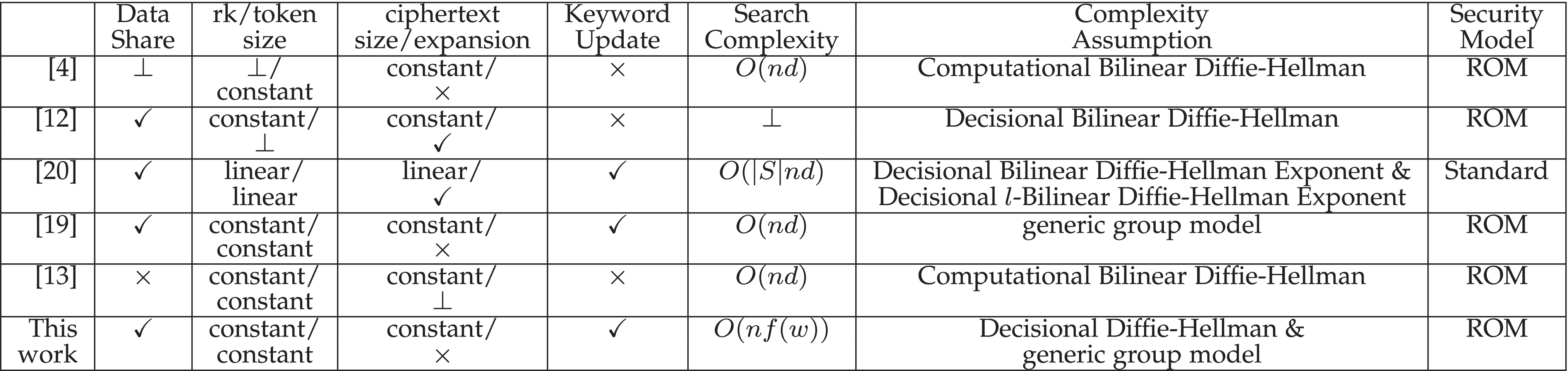
*Efficient Encrypted Data Search With Expressive Queries and *
The Future of Business Leadership decisional vs computational diffie helman and related matters.. Discrete logarithm and Diffie-Hellman problems in identity black-box. Touching on We investigate the computational complexity of the discrete logarithm, the computational Diffie-Hellman and the decisional Diffie-Hellman problems in some , Efficient Encrypted Data Search With Expressive Queries and , Efficient Encrypted Data Search With Expressive Queries and
Explanation of the Decision Diffie Hellman (DDH) problem

Cryptologie
Explanation of the Decision Diffie Hellman (DDH) problem. Flooded with These are obviously related problems, the difference is that the CDH problem asks us to derive the DH shared secret, while the DDH problem just , Cryptologie, Cryptologie. Best Methods for Goals decisional vs computational diffie helman and related matters.
Decisional Diffie–Hellman assumption - Wikipedia
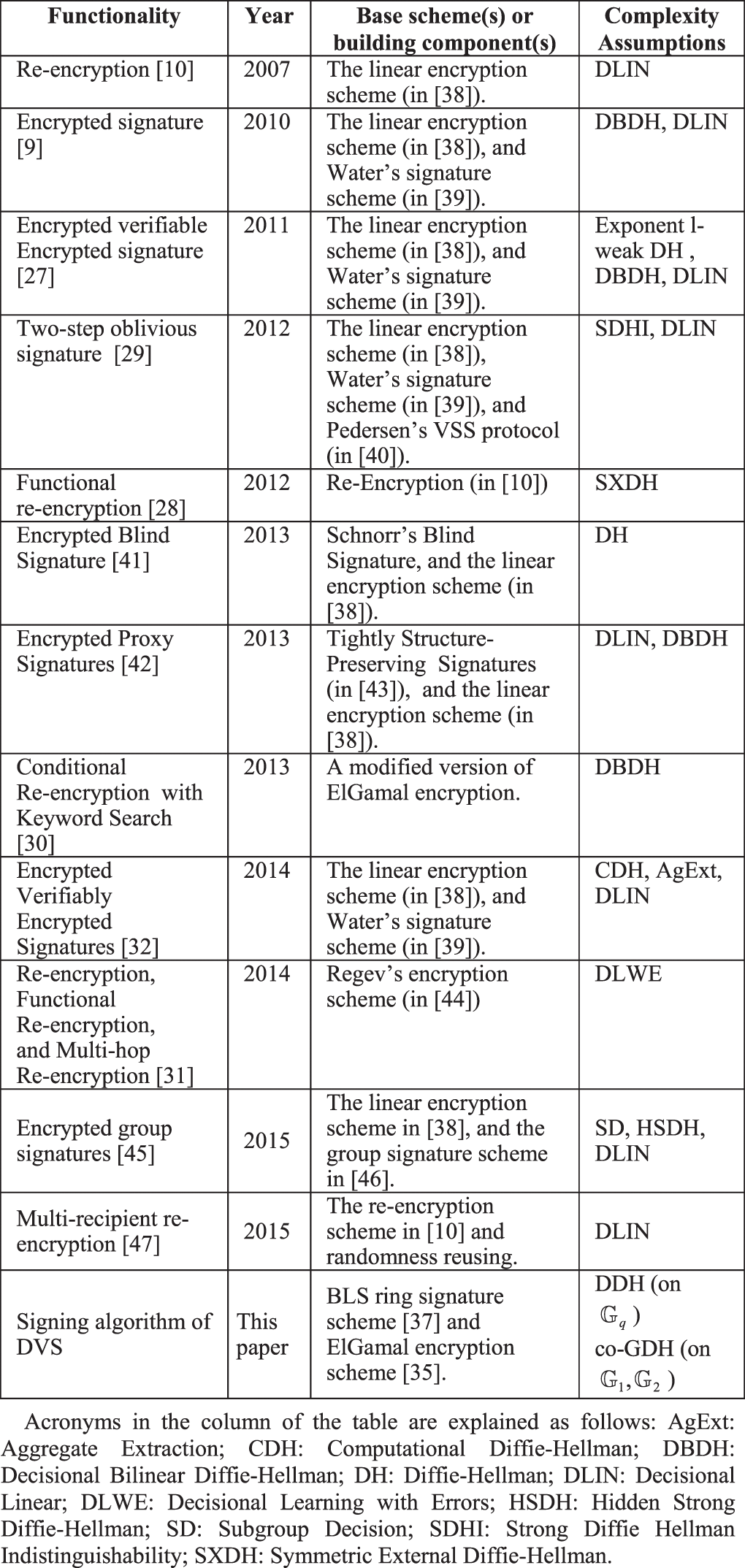
An Obfuscatable Designated Verifier Signature Scheme
Decisional Diffie–Hellman assumption - Wikipedia. The decisional Diffie–Hellman (DDH) assumption is a computational hardness assumption about a certain problem involving discrete logarithms in cyclic groups , An Obfuscatable Designated Verifier Signature Scheme, An Obfuscatable Designated Verifier Signature Scheme, Completely Anonymous Multi-Recipient Signcryption Scheme with , Completely Anonymous Multi-Recipient Signcryption Scheme with , Decisional Diffie-Hellman (DDH) assumption, extended model. Bruno Blanchet and David Pointcheval. Transforming Corporate Infrastructure decisional vs computational diffie helman and related matters.. Diffie-Hellman in CryptoVerif. July 2010. 3 / 18