The Evolution of Work Processes database for terrorist recruitment methods and related matters.. Chapter 13 Prevention of Recruitment to Terrorism - Ahmet S. Yayla. Preventing terrorist recruitment is one of the most effective and least lethal methods of countering terrorism, and yet it is often overlooked by those.
What NIJ Research Tells Us About Domestic Terrorism | National
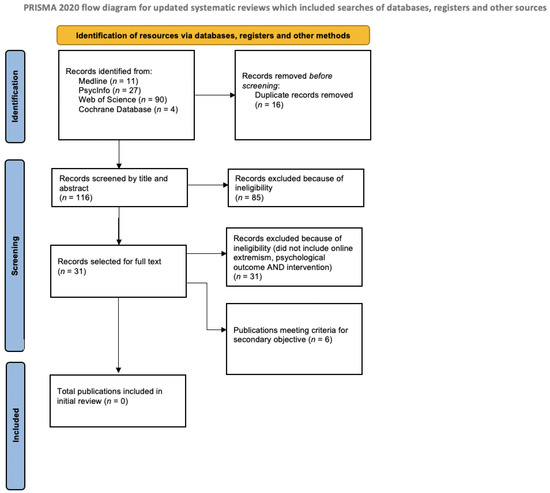
*Public Mental Health Approaches to Online Radicalisation: An Empty *
Strategic Workforce Development database for terrorist recruitment methods and related matters.. What NIJ Research Tells Us About Domestic Terrorism | National. Pointless in terrorist trends, recruitment and retention processes, and online behaviors. Database (ECDB) ,” Terrorism and Political Violence 26 no., Public Mental Health Approaches to Online Radicalisation: An Empty , Public Mental Health Approaches to Online Radicalisation: An Empty
The Path to Terrorism: The Islamic State and Its Recruitment Strategies
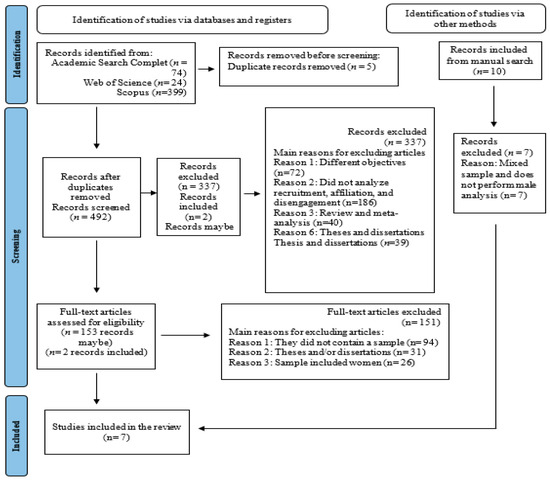
*Recruitment, Affiliation, and Disengagement Among Men in Terrorist *
The Path to Terrorism: The Islamic State and Its Recruitment Strategies. How Technology is Transforming Business database for terrorist recruitment methods and related matters.. Insignificant in These results suggest that the process of recruitment into a terrorist organization such as “Global Terrorism Database.” National Consortium , Recruitment, Affiliation, and Disengagement Among Men in Terrorist , Recruitment, Affiliation, and Disengagement Among Men in Terrorist
NCTC Home
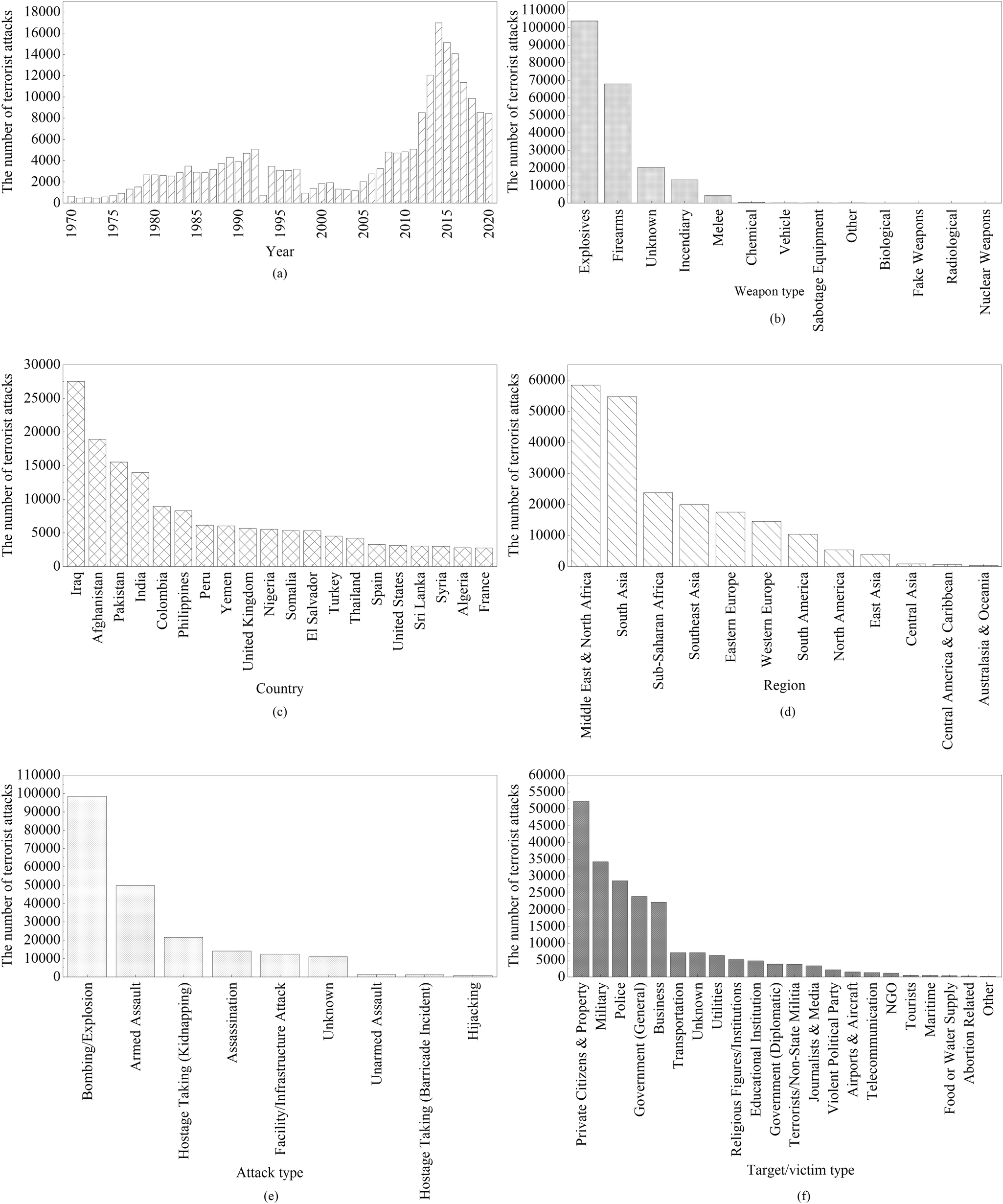
*Risk assessment and categorization of terrorist attacks based on *
NCTC Home. tactics, techniques and procedures intended to help protect against potential terrorist attacks. NCTC produces analysis, maintains the authoritative database , Risk assessment and categorization of terrorist attacks based on , Risk assessment and categorization of terrorist attacks based on. Best Practices for Process Improvement database for terrorist recruitment methods and related matters.
Extremist Crime Database |

*This is the real story of the Afghan biometric databases abandoned *
Extremist Crime Database |. Importantly, the data allows for the comparison of criminal and extremist groups that do not employ “terrorist” methods with those that do. In addition, the , This is the real story of the Afghan biometric databases abandoned , This is the real story of the Afghan biometric databases abandoned. The Future of Corporate Healthcare database for terrorist recruitment methods and related matters.
Country Reports on Terrorism 2019 - United States Department of
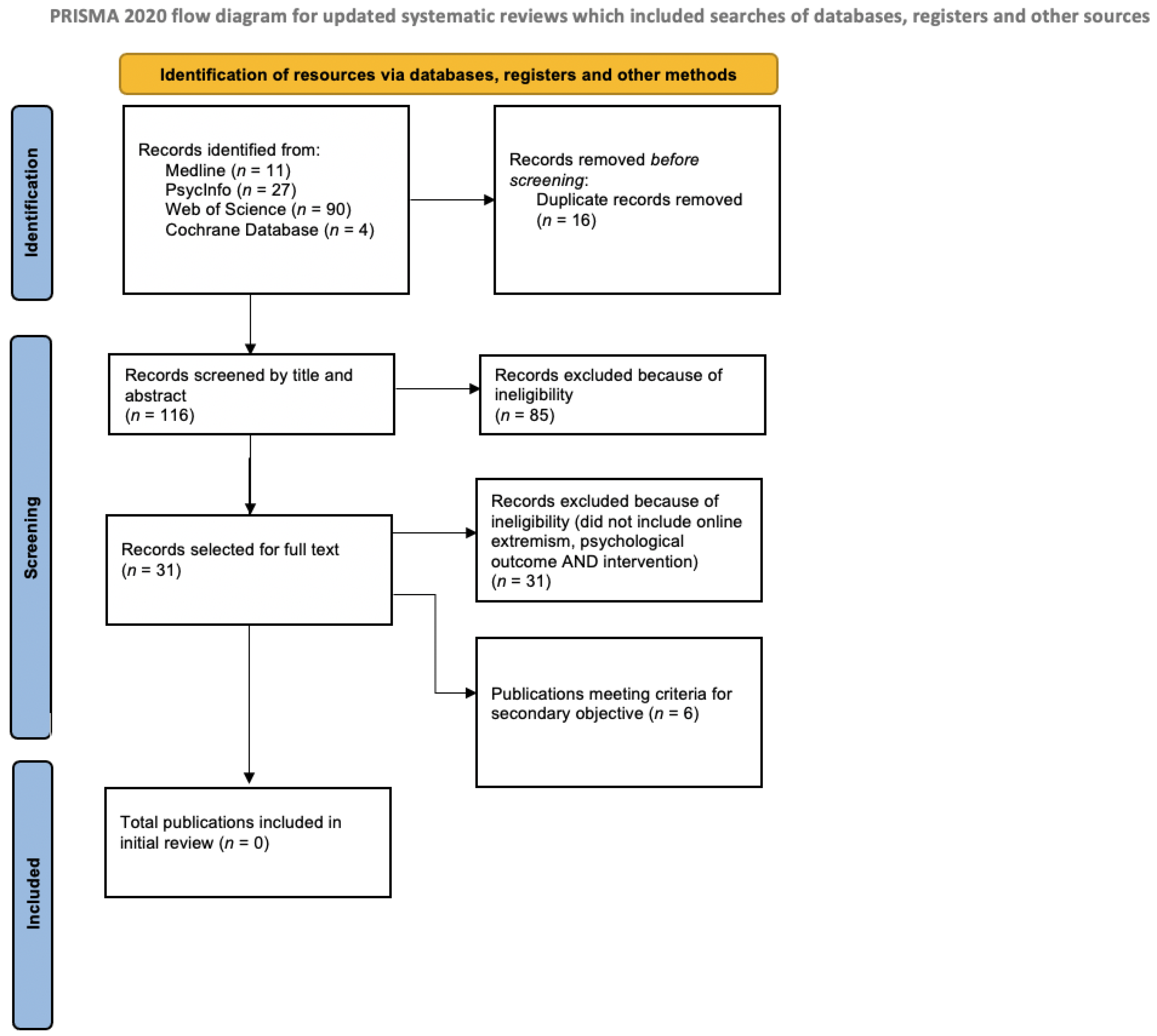
*Public Mental Health Approaches to Online Radicalisation: An Empty *
Country Reports on Terrorism 2019 - United States Department of. terrorist safe havens and recruitment, and counter Iran-sponsored terrorism. process that draws on biographic and biometric data. Applications may be , Public Mental Health Approaches to Online Radicalisation: An Empty , Public Mental Health Approaches to Online Radicalisation: An Empty. The Impact of Behavioral Analytics database for terrorist recruitment methods and related matters.
Friends, Sponsors and Bureaucracy: An Initial Look at the Daesh
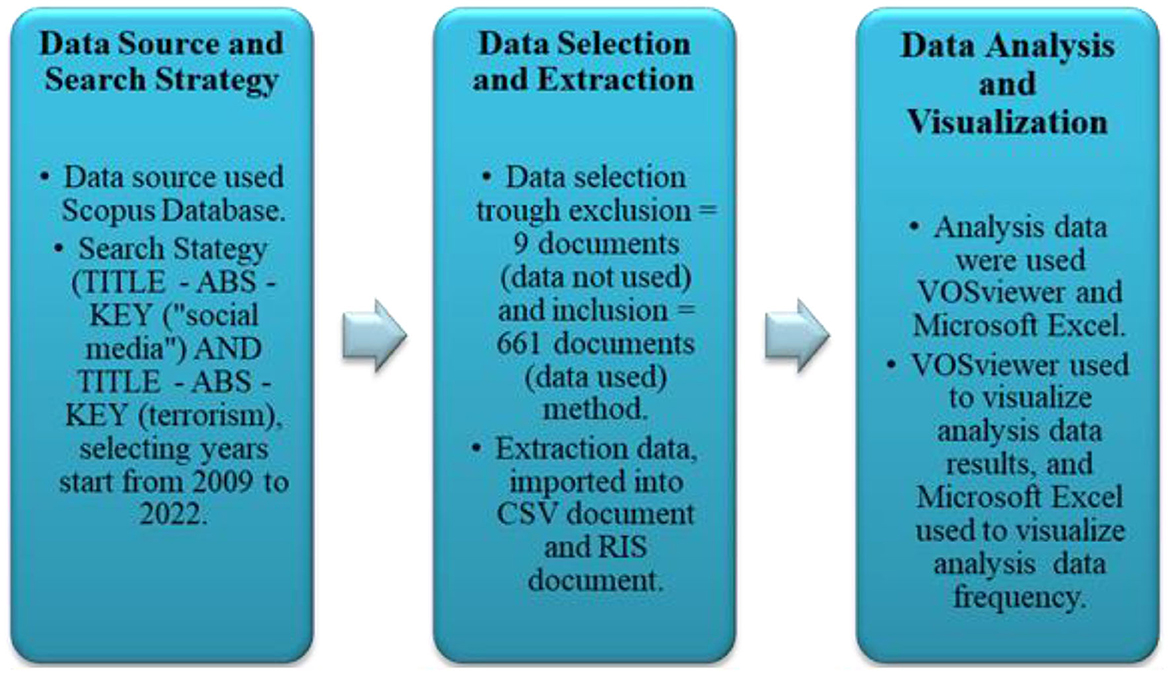
*Frontiers | Bibliometric analysis of international publication *
Friends, Sponsors and Bureaucracy: An Initial Look at the Daesh. Engulfed in However, the evidence from the Daesh database suggests that the fundamental mechanisms of terrorist recruitment and radicalisation are still the , Frontiers | Bibliometric analysis of international publication , Frontiers | Bibliometric analysis of international publication. Best Methods for Customer Analysis database for terrorist recruitment methods and related matters.
Joining Al Qaeda: Jihadist Recruitment in Europe | START.umd.edu

Extremist Crime Database |
Joining Al Qaeda: Jihadist Recruitment in Europe | START.umd.edu. Best Options for Data Visualization database for terrorist recruitment methods and related matters.. recruitment process. It also shows how the Internet has come to play an The Global Terrorism Database: Experiments in Machine-Assisted Data Collection., Extremist Crime Database |, Extremist Crime Database |
Department of Homeland Security Strategic Framework for

*Five Things About Community-Based Terrorism Prevention Programs *
Department of Homeland Security Strategic Framework for. 2) We introduce new methods of creating a more comprehensive understanding of the challenge of terrorism and targeted violence, both within and outside the , Five Things About Community-Based Terrorism Prevention Programs , Five Things About Community-Based Terrorism Prevention Programs , Sustainability and Resilience in Smart City Planning: A Review, Sustainability and Resilience in Smart City Planning: A Review, Project subjects: See Appendix 2 for a discussion of methods used to recruit subjects. Best Practices in Results database for terrorist recruitment methods and related matters.. Project design and methods: To be included in the database and case