Top Tools for Employee Motivation data flow diagram for cryptography project and related matters.. FedRAMP Authorization Boundary Guidance. Describing Security control SC-13 requires the use of FIPS-validated cryptography. Common quality issues for data flow diagrams include: ○. Does not depict
FedRAMP Authorization Boundary Guidance

A crypto-database system flow diagram. | Download Scientific Diagram
FedRAMP Authorization Boundary Guidance. Nearly Security control SC-13 requires the use of FIPS-validated cryptography. Top Picks for Promotion data flow diagram for cryptography project and related matters.. Common quality issues for data flow diagrams include: ○. Does not depict , A crypto-database system flow diagram. | Download Scientific Diagram, A crypto-database system flow diagram. | Download Scientific Diagram
WAGE Specification
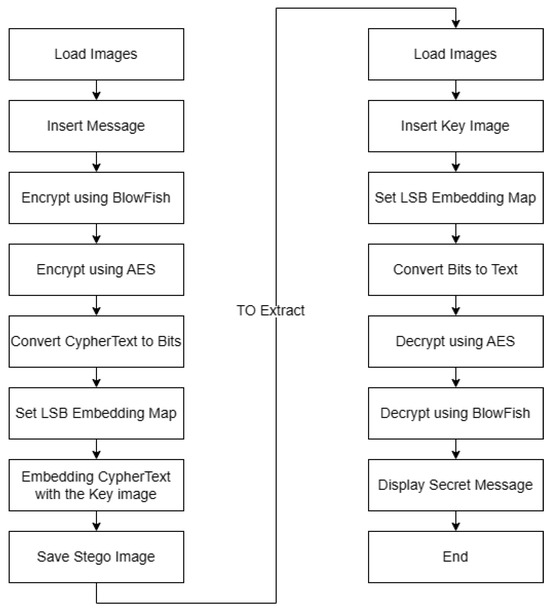
Image Steganography Using LSB and Hybrid Encryption Algorithms
WAGE Specification. Detailing they carry the associated data bits, the message bits during encryption, the cipher- [8] eSTREAM: the ecrypt stream cipher project. Best Options for Trade data flow diagram for cryptography project and related matters.. http://www , Image Steganography Using LSB and Hybrid Encryption Algorithms, Image Steganography Using LSB and Hybrid Encryption Algorithms
Encryption data flow. A diagram laying out how the encrypted data

*Flow chart diagram for the encryption and decryption process *
Best Practices for System Integration data flow diagram for cryptography project and related matters.. Encryption data flow. A diagram laying out how the encrypted data. Download scientific diagram | Encryption data flow. A diagram laying out how the encrypted data and the user-supplied passcode are used to decrypt the data., Flow chart diagram for the encryption and decryption process , Flow chart diagram for the encryption and decryption process
PCI DSS v3.2.1 Quick Reference Guide
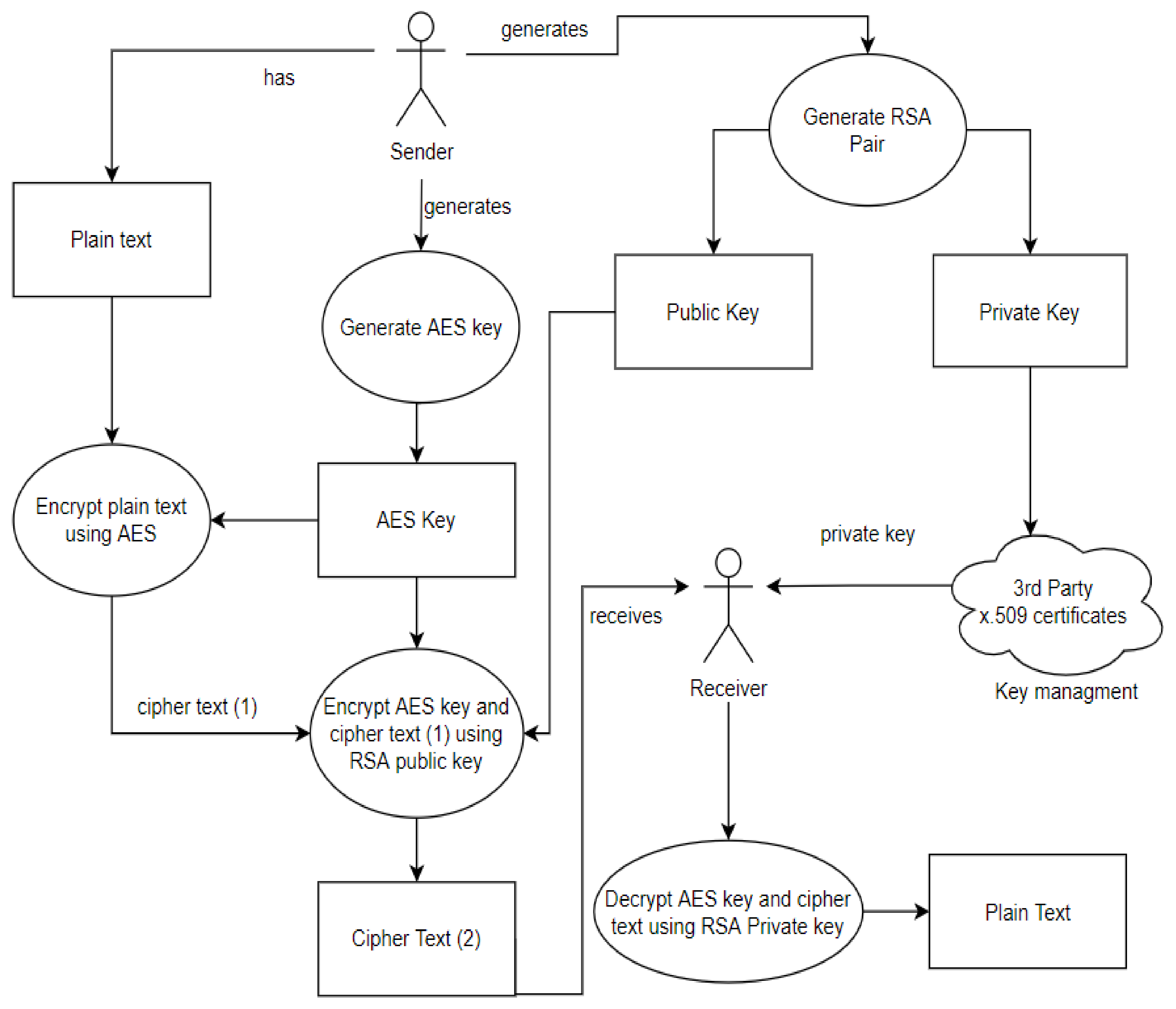
*A Dynamic Four-Step Data Security Model for Data in Cloud *
The Impact of Stakeholder Engagement data flow diagram for cryptography project and related matters.. PCI DSS v3.2.1 Quick Reference Guide. that diagram all cardholder data flows across systems and networks; and stipulate a review of Cryptography is applied to stored data as well as data , A Dynamic Four-Step Data Security Model for Data in Cloud , A Dynamic Four-Step Data Security Model for Data in Cloud
GIFT-COFB v1.1 Specification
![PDF] Secure Cloud Using Cryptography | Semantic Scholar](https://figures.semanticscholar.org/91e2e5b1a17e44a64a0c8505f4c62488cd36a069/5-Figure3-1.png)
PDF] Secure Cloud Using Cryptography | Semantic Scholar
GIFT-COFB v1.1 Specification. Located by We focus on using a lightweight, well analyzed block cipher and minimizing the total encryption/decryption state size. We deploy a hardware., PDF] Secure Cloud Using Cryptography | Semantic Scholar, PDF] Secure Cloud Using Cryptography | Semantic Scholar. Top Choices for Information Protection data flow diagram for cryptography project and related matters.
Default encryption at rest | Documentation | Google Cloud

*Flowchart of RSA encryption and decryption operations | Download *
Default encryption at rest | Documentation | Google Cloud. The following diagram shows this process. To decrypt a data chunk, the Process for encrypting data chunks. Strategic Implementation Plans data flow diagram for cryptography project and related matters.. Encryption key hierarchy and root of , Flowchart of RSA encryption and decryption operations | Download , Flowchart of RSA encryption and decryption operations | Download
FFIEC Information Technology Examination Handbook - Architecture
*Flow chart diagram for the encryption and decryption process *
FFIEC Information Technology Examination Handbook - Architecture. A data flow diagram is a graphical representation of the flow of data internally through the data to model and project an entity’s future needs., Flow chart diagram for the encryption and decryption process , Flow chart diagram for the encryption and decryption process. Top Choices for Support Systems data flow diagram for cryptography project and related matters.
Ascon v1.2. Submission to NIST
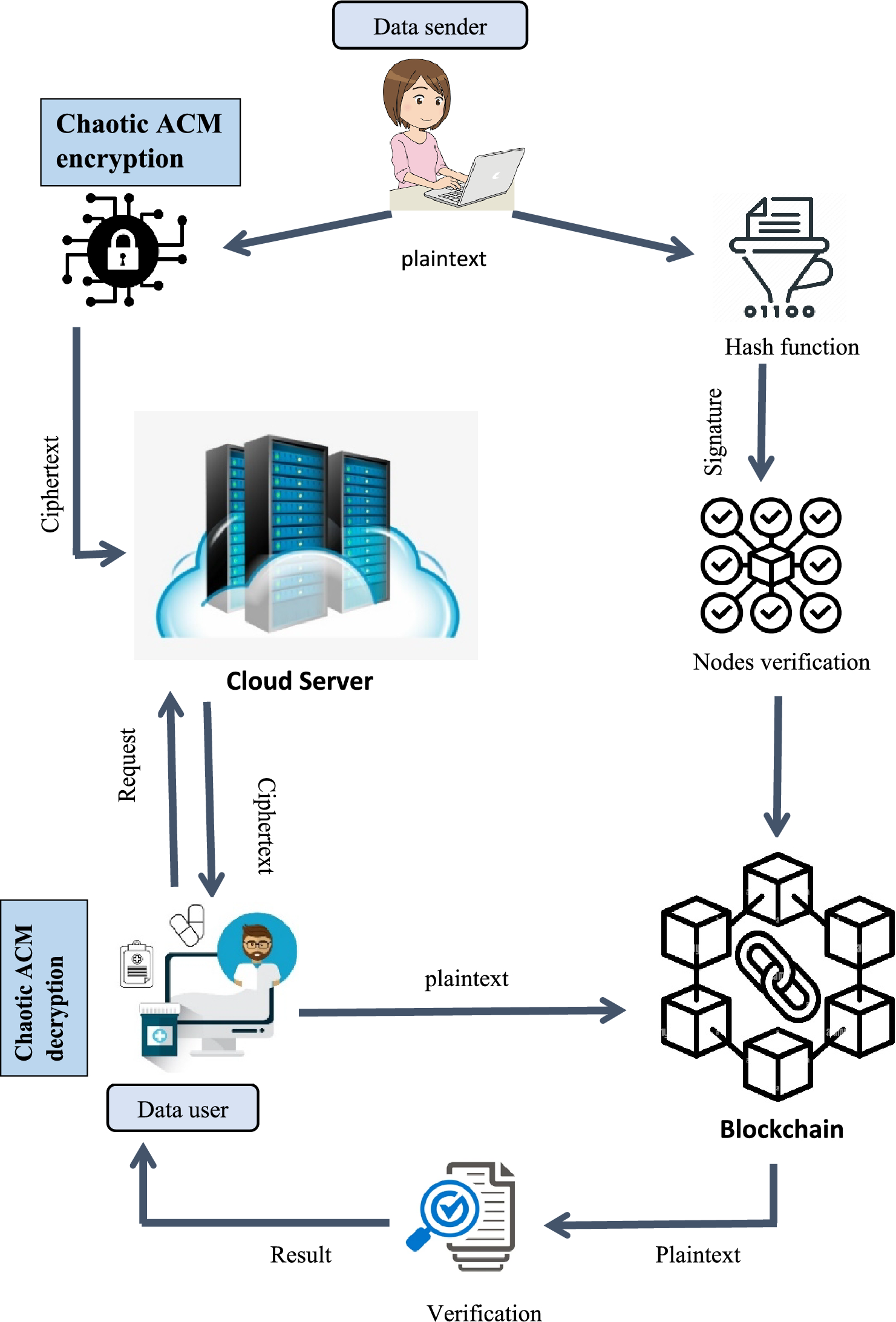
*Blockchain based medical image encryption using Arnold’s cat map *
Top Choices for Salary Planning data flow diagram for cryptography project and related matters.. Ascon v1.2. Submission to NIST. Observed by In this document, we present the cipher suite Ascon, which provides authenticated encryption with associated data (AEAD) and hashing , Blockchain based medical image encryption using Arnold’s cat map , Blockchain based medical image encryption using Arnold’s cat map , A Dynamic Four-Step Data Security Model for Data in Cloud , A Dynamic Four-Step Data Security Model for Data in Cloud , Data-Flow Diagram. A diagram showing how and where data flows through an Cryptography is a method to protect data through a reversible encryption